Here are the steps to configure your SQL Server to allow your Protected Users to connect to the Database using the Integrated Security authentication method.
According to Microsoft Protected Users blocks the use of NTLM hashes It is however possible to configure SQL Server to also use Kerberos for Integrated Security The good news is that this is supported out-of-the-box by Remote Desktop Manager.
For SQL Server to support Kerberos authentication, SPNs need to be created. By default, the service runs under accounts that lack the required permissions. We suspect you might have the following messages when SQL Server starts (you can see the logs in SSMS under Management SQL Server Logs).
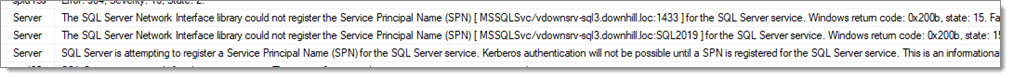
You will need to configure the SQL Server service to run under Network Service as it has the necessary permissions According to this article it is also possible to grant the permissions to create SPNs to a service account. You will also need to change the account in SQL Server Configuration Manager.
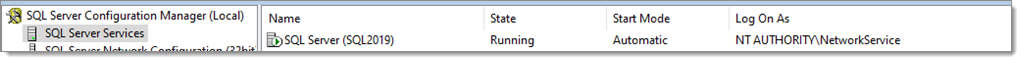
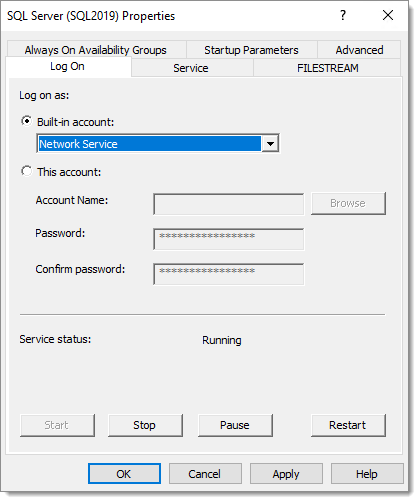
However, on our server, SQL Server was still reporting that it was unable to register the SPNs. We used Microsoft Kerberos Configuration Manager for SQL Server to fix the SPNs. It shows clickable buttons in the Action columns.
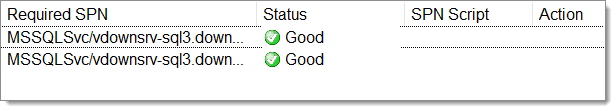
After restarting the SQL Server service, you should see “The SQL Server Network Interface library successfully registered the Service Principal Name (SPN) [ MSSQLSvc/vdownsrv-sql3.downhill.loc:1433 ] for the SQL Server service.” in the logs.
At this point the connection should work again in Remote Desktop Manager.