Microsoft RDP API hooking is available and enabled by default in Remote Desktop Manager. API hooking is required to extend the functionality of the Microsoft RDP client in both embedded (ActiveX) and external modes (mstsc).
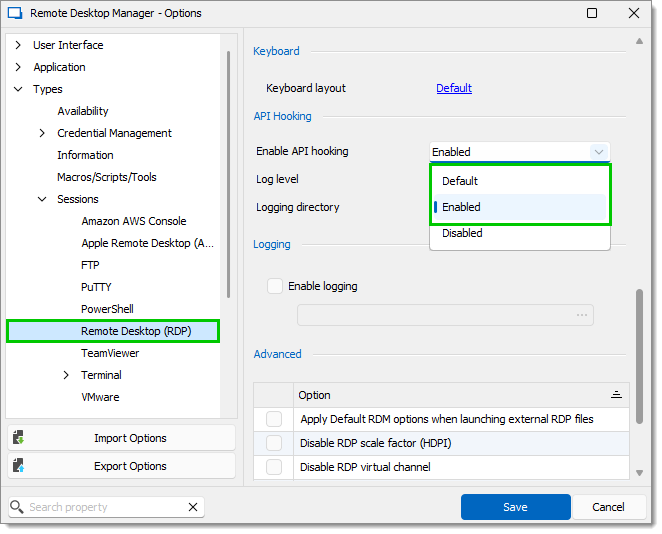
If you have disabled it, you can enable it again by going in Remote Desktop Manager File – Settings – Types – Sessions – Remote Desktop (RDP) – API hooking and setting Enable API hooking to Enabled or Default.
Restart Remote Desktop Manager to apply the change.
The EnableRDPHooking policy overrides the Enable API hooking setting. If it is not configured (no registry key), the value from the Remote Desktop Manager option will be used. A value of "0" indicates that RDP hooking is disabled, while a value different than "0" indicates that RDP hooking is enabled. This enables the administrator to force either setting or allow the local configuration to be effective.
See all policies including this one in Apply policies.
The Microsoft RDP API hooking module will be loaded on the first Microsoft RDP connection. In the unlikely event that you notice instability with API hooking enabled, disable it and then contact the customer support team to report the issue.
Microsoft RDP API hooking makes it possible to log internal events and options that were not possible previously. If you encounter issues, go to File – Settings – Types – Remote Desktop – API hooking and set the Log level to Debug Restart Remote Desktop Manager to obtain log files under %LocalAppData%\MsRdpEx which you can then send to the customer support team to help diagnose issues.
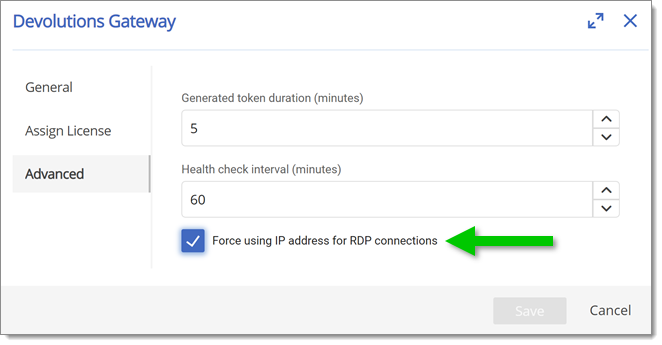
Microsoft RDP API hooking should be enabled for Devolutions Gateway connections, as it fixes the server name used for validation by the RDP client. This can fix the Kerberos name mismatch issue, but it can also fix TLS certificate validation. This is particularly important for customers using the Force using IP address for RDP connections option, as it fixes the underlying issue:
Once Microsoft RDP API hooking is enabled, the Force using IP address for RDP connections option should be disabled. In cases where the Kerberos name mismatch issue occurred, Kerberos should now work just fine.
RDP API hooking fixes the issue where the RDP Always prompt for password upon connection group policy prevents credential injection from Remote Desktop Manager This group policy is intended to force mstsc.exe to prompt fresh credentials on every connection, but it has the unintended side effect of breaking credential injection. A workaround is applied through API hooking to make it work.