This article covers Remote Desktop Manager versions 2022.1 and later. If you are using an earlier version, please consult Configure an older Remote Desktop Manager version AD Interactive (with MFA support) instead.
Active Directory Interactive (with MFA support) allows you to authenticate to your Microsoft Azure SQL data source using your Office 365 credentials with multi-factor authentication (MFA).
When creating Azure SQL Active Directory users, you must be signed in with an Entra ID account. If not, the operation will fail and an error message will be displayed.
Use the server’s defined Entra ID administrator account to create your first Remote Desktop Manager administrator user. Once created, you can use this new account to create additional ones.
-
In Remote Desktop Manager, go to File – Data sources and click on Add a new data source.
-
Select the Microsoft Azure SQL data source type.
-
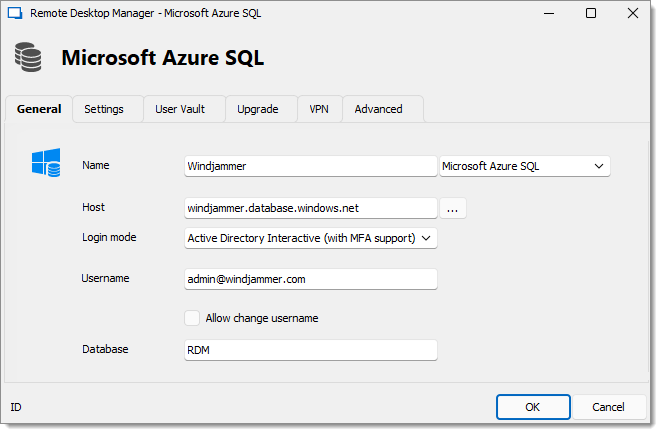
Specify the Name and Host of your data source.
-
In the Login mode drop-down menu, select Active Directory Interactive (with MFA support).
-
In the Username field, paste the Active Directory admin email you created in Microsoft Azure SQL Database.
On the first connection, the username must be that of the Entra ID administrator, as defined in Configure the Entra ID administrator. Once additional AD users are added in Remote Desktop Manager, they will be able to connect as well.
If you receive the error message “Unable to connect to the database! Login failed for user '<token-identified principal>'.“ , verify that the username is spelled correctly.
-
Enter the name of the Database you want to authenticate to.
-
Click Add.
When you choose Active Directory Interactive (with MFA support), Remote Desktop Manager has no control over the login prompts. The authentication request is sent to the Microsoft library, and all subsequent prompts are handled entirely by Microsoft.
Here are some considerations:
Have any conditional access policies been added or modified recently that could explain a change in behavior?
If you're using an Entra ID-joined machine, you might try using Active Directory Integrated to see if it provides a smoother experience.