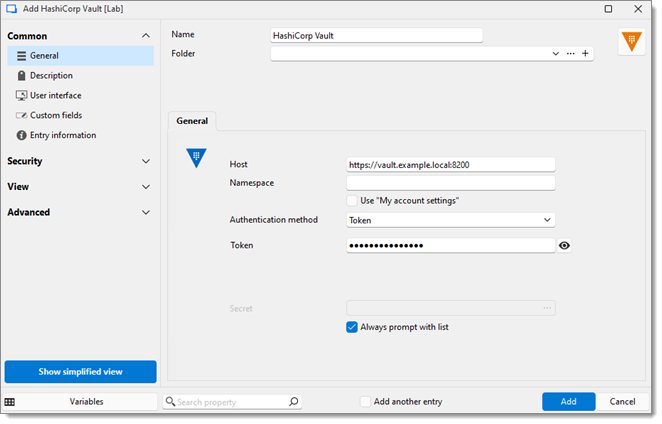
Linking your secrets in HashiCorp Vault to Remote Desktop Manager sessions allows credentials to be injected automatically when launching connections, eliminating the need for manual copying and reducing the risk of exposure. This topic covers the settings for the entry located under Add new entry – Credential management – HashiCorp Vault.
SETTINGS | DESCRIPTIONS |
|---|---|
Host | The URL or IP address of your HashiCorp Vault instance. |
Namespace | Specifies the namespace within your HashiCorp Vault instance. Use this if your Vault environment is configured with enterprise namespaces to logically separate data or manage multi-tenancy. Leave blank if not applicable. |
Use "My account settings" | Enable this option to reuse account settings you have configured under File – My account settings. |
Authentication method | Select the authentication method to align with your environment’s identity policies:
|
Secret | When enabled, this will force Remote Desktop Manager to prompt the user to select a secret each time a connection is launched. Useful if different credentials are used frequently. |
Learn how to retrieve and inject stored credentials from HashiCorp Vault directly into your sessions. Supported session types include RDP, SSH, VNC, SFTP, and more.
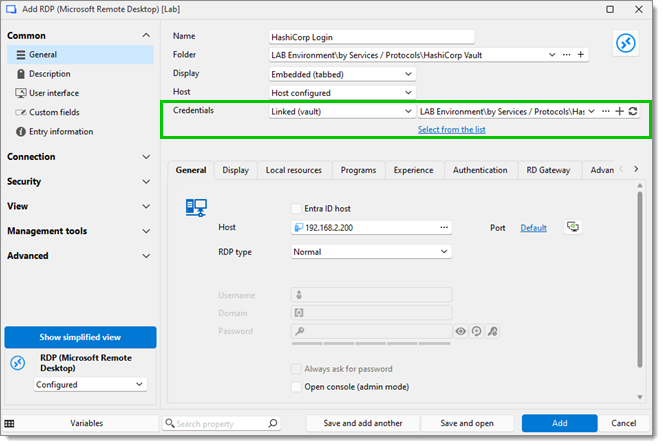
In this example, we will create an RDP session. Go to Add new entry – Session – RDP (Microsoft Remote Desktop). In the Credentials field, select Linked (vault) and choose the HashiCorp Vault entry you previously created that contains your credentials. Once you have filled in the required RDP settings, click Add or Save and open to launch the session.
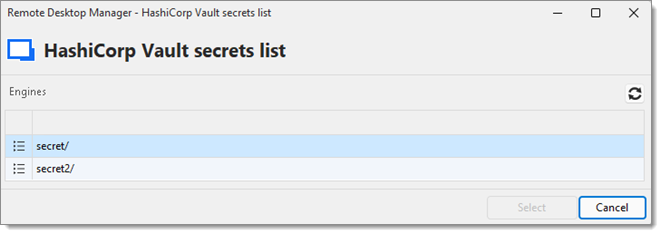
Select the secret in the HashiCorp Vault secrets list to open the RDP session.