In version 2023.3, privileges obtained through JIT elevation using an Entra ID (Azure) provider were not correctly revoked after elevation.
If the PAM check-in was done automatically by the scheduler (e.g., when the timer of a checkout was elapsed) it is possible the user is still part of the group it was originally elevated as.
Solution
- Log in with an administrator account in the web interface for Devolutions Server.
- Go to Administration – Privileged Access – Providers.
- Click the Settings button on the Entra ID (Azure) provider.
- Go to the Settings tab and review the groups in the Just-In-Time (JIT) elevation section.
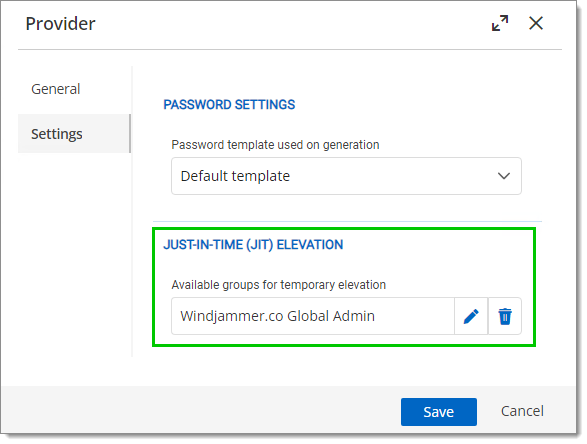
Just-In-Time (JIT) elevation groups - In Microsoft Azure go to Azure – Microsoft Entra ID – Groups.
- Review the desired group to make certain the user accounts used during the JIT elevation process are no longer part of the group(s).







