The Logs section provides tools to view Activity, Data Sources, Administration and Last Usage Logs. The Deleted Entries section is where you will manage all the deleted entries from the users.
You can refine your search with the filters for each report and click the Export button of each section to create a CSV report.
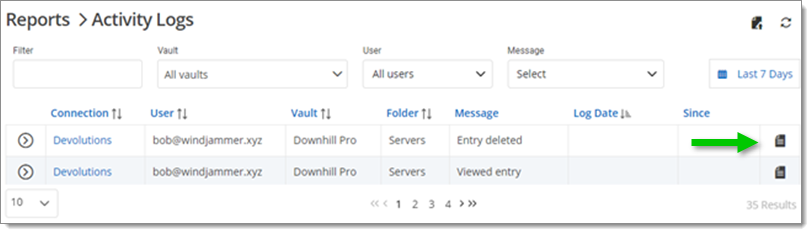
The Activity Logs report displays specific vault actions on the activity of selected users or of all of your users. Activity Message are listed in a drop down menu to choose from and refine your search.
Click the Log Entry button to view more information about the activity.
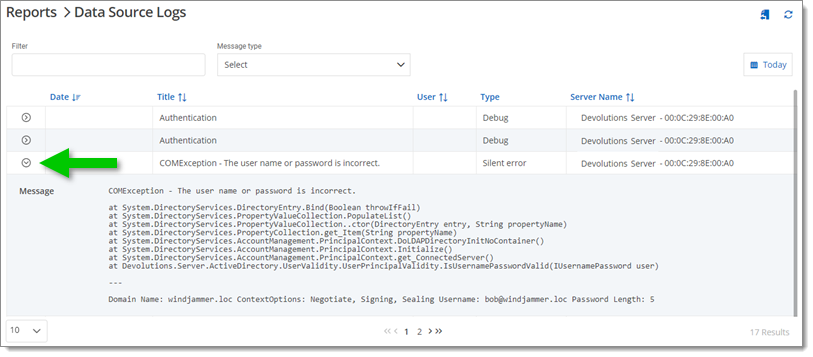
The Data Sources Logs displays the logs of the Devolutions Server data source. For more information on a specific log, click the arrow at the beginning of the line.
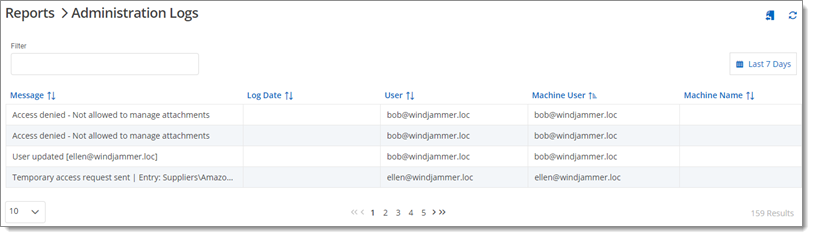
The Administration Logs keeps track of administrative level activities, such as access denied, temporary access request and user or user group update.
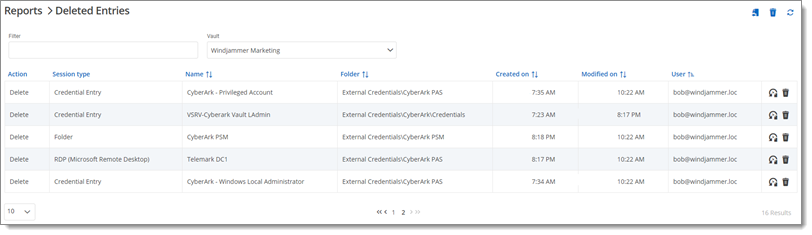
The Deleted Entries lists every entry deleted in the data source, including the folder it originated from, when and whom deleted it. Refine your search by vault with the filter and click Resurrect Entry to recover the entry in its original vault and folder.
Once you confirm to delete an entry from the Deleted Entries lists, it will be deleted completely from the Devolutions Server data.
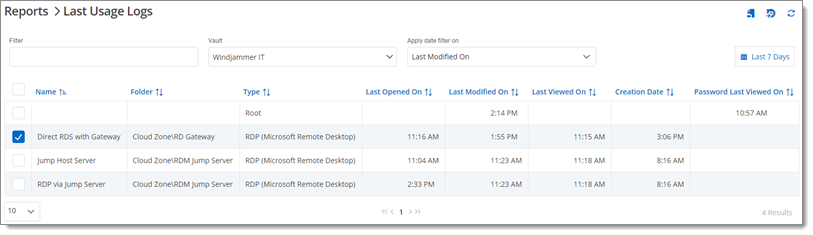
The Last Usage Logs displays the time and date of the last modification done on an entry.
From the list you can also move the entries shown to another vault. For this, select the entries and click the Move To vault button.
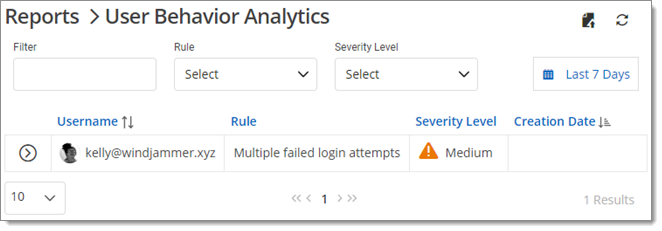
The User Behavior Analytics allows you to track user behavior. Detect multiple failed login attempts and connections from a country or location that deviates from established patterns. View when emergency access is used and when login requests are made through the Tor Browser.