A Devolutions Server instance requires several accounts to run its various services. Instances support Active Directory domain accounts or SQL accounts paired with local service accounts to run its services.
The account names in this topic are only suggestions.
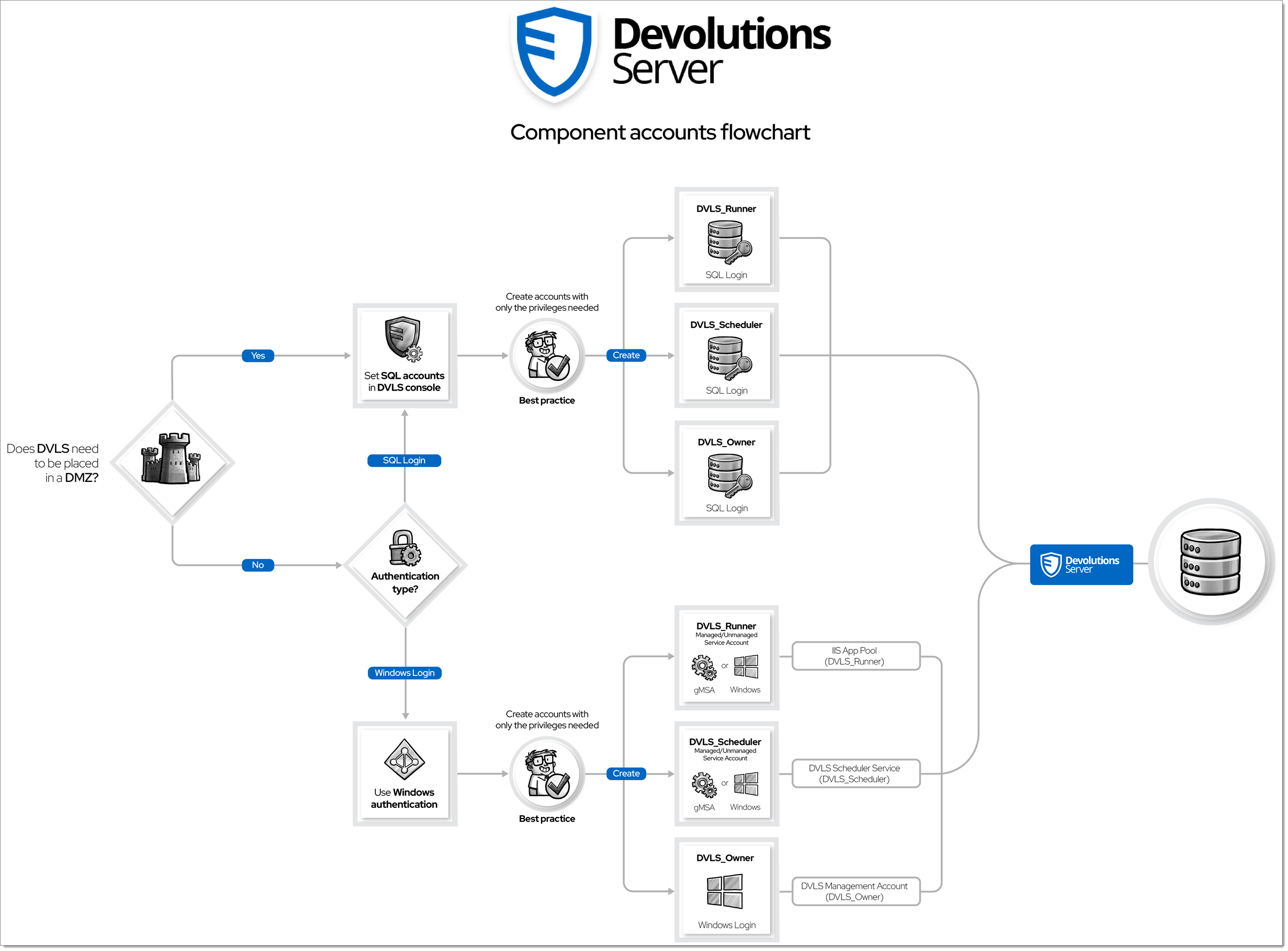
Devolutions Server supports the use of integrated authentication for Windows accounts. Typically, these accounts are managed in on-premise Active Directory environments or cloud-hosted Azure Entra ID.
It is recommended to use separate accounts for the different roles.
ACCOUNT | TYPE | PURPOSE | REQUIREMENTS | ||||||
|---|---|---|---|---|---|---|---|---|---|
DVLS_Owner | Active Directory or local Windows | A local administrative Windows account must exist on the Devolutions Server host system to properly install and administer it (via the Devolutions Server Console application). Used to launch the Devolutions Server Console application to install a Devolutions Server instance. |
| ||||||
DVLS_Runner | Active Directory | The account is assigned to the IIS application pool running the Devolutions Server instance and is assigned the least privileges upon installation of the instance. After installing the application, the configuration must be performed directly on the IIS application pool. Once the pool has been configured, the Devolutions Server Console should be used to assign the least privileges required for the user. |
| ||||||
DVLS_Scheduler | Active Directory | This account is required to run background tasks within a Devolutions Server instance, like the Scheduler service, and is assigned the least privileges upon installation of the instance. Configured within the Devolutions Server Console during an instance installation. |
| ||||||
DVLS_ADAuth | Active Directory | An optional account that is only required if Windows authentication is enabled for a Devolutions Server instance. Once it is installed, you may configure available authentication methods in the web UI under Administration – Configuration – Server settings – Authentication. |
|
Devolutions Server supports SQL logins for non-domain joined Windows computers, or if non-domain accounts are to be used. It is recommended that you use separate accounts for the different roles.
It is recommended to use separate accounts for the different roles.
ACCOUNT | TYPE | PURPOSE | REQUIREMENTS |
|---|---|---|---|
Local administrator account | Local Windows | A local administrative Windows account must exist on the Devolutions Server host system to properly install and administer it (via the Devolutions Server Console application). Used to launch the Devolutions Server Console application to install a Devolutions Server instance. |
|
DVLS_Owner | SQL Login | An SQL Login account with rights to create a database and assign the necessary permissions to the new Devolutions Server instance. |
|
DVLS_Runner | SQL Login | The IIS application pool runs as the Windows local | |
DVLS_Scheduler | SQL Login | This account is required to run background tasks within a Devolutions Server instance, like the Scheduler service, and is assigned the least privileges upon installation of the instance. The Windows Service runs as the Windows | |
DVLS_ADAuth | Active Directory | An optional account that is only required if Windows authentication is enabled for a Devolutions Server instance. Once it is installed, you may configure available authentication methods in the web UI under Administration – Configuration – Server settings – Authentication. |
|
Devolutions Server for Linux (Beta) does not require the same number of accounts as a Windows instance. It runs as a Kestrel application with a self-contained scheduler. Therefore, a single Linux user is required to run a Devolutions Server instance.
It is recommended to use separate accounts for the different roles.
ACCOUNT | TYPE | PURPOSE | REQUIREMENTS |
|---|---|---|---|
DVLS_Owner | Linux User | A sudo-enabled account is required to run the installation scripts to install a Devolutions Server instance. | |
DVLS_Runner | Linux User | The Linux account is assigned to the running Devolutions Server instance controlled by a SystemD unit file. | |
DVLS_ADAuth | Active Directory | An optional account that is only required if Windows authentication is enabled for a Devolutions Server instance. Once it is installed, you may configure available authentication methods in the web UI under Administration – Configuration – Server settings – Authentication. |
|