When trying to sign in to your Devolutions Hub Business using Microsoft Single Sign-On (SSO), you may encounter the following error message: "The client ID or secret supplied by your organization is invalid, please contact an administrator of your organization."
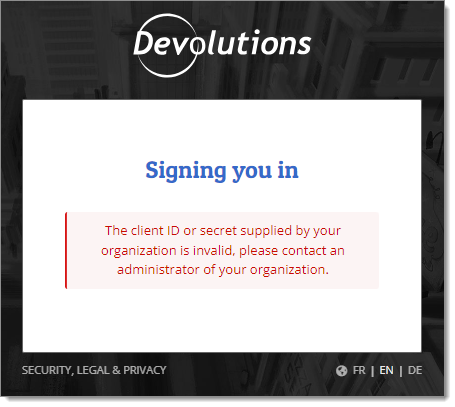
This most likely means that your client secret is expired in the Microsoft Azure Portal. The solution is to create a new secret and change it in your Devolutions Hub Business SSO configuration.
-
In a new web browser page, open your Microsoft Azure Portal and sign in to your account.
-
Select Microsoft Entra ID (formerly Azure Active Directory) in the Azure services section. If you do not see it, click on More services to make other services appear.
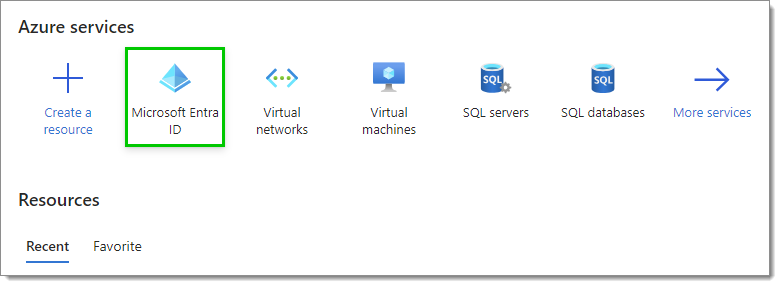
Microsoft Entra ID service -
Click on App registrations in the left menu.
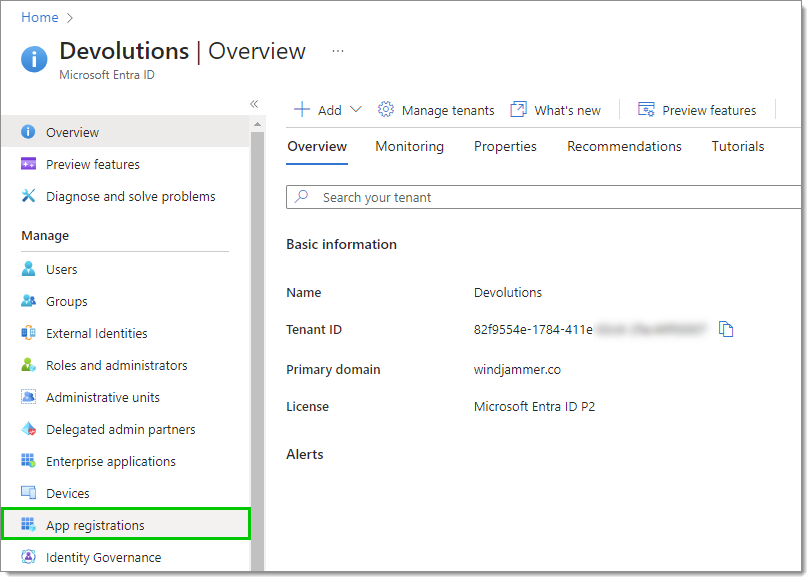
App registrations -
In the list, click on the application that you configured single sign-on with in your hub to go to its overview.
-
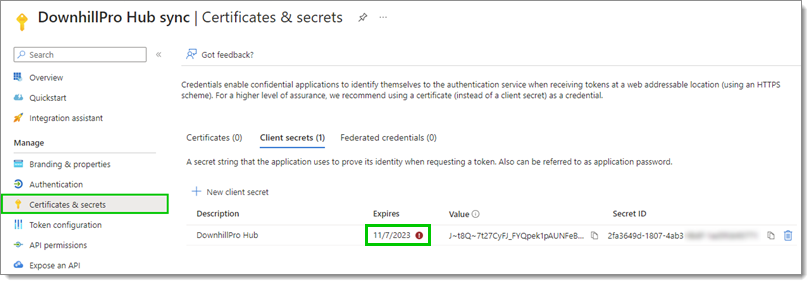
Click on Certificates & secrets in the left menu.
-
Locate the secret that is currently used in your Devolutions Hub Business SSO configuration and see if it is expired in the Expires column.
Enterprise applications
If it is indeed expired, this is most likely the cause of your connection issue. You need to create a new client secret and change it in your Devolutions Hub Business SSO configuration by following the next steps.
If the client secret is not expired, the issue may come from your client ID. Verify that it matches the one in your SSO configuration then try logging in again.
-
Click on New client secret.
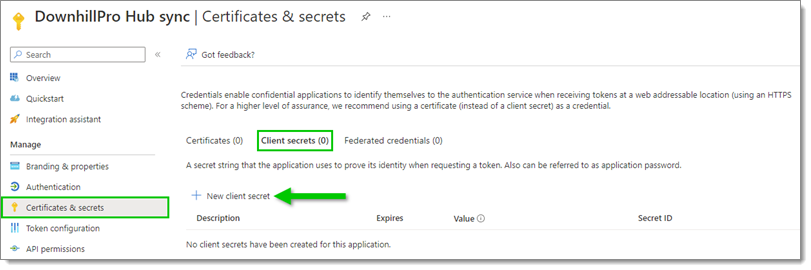
New client secret -
In the Add a client secret window, enter a Description (for example, the name of your Enterprise app) and select an expiration date for this client secret, as per your best internal security practices.
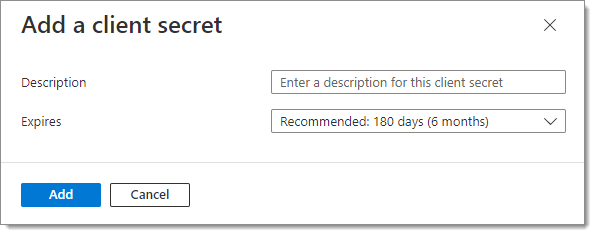
Add a client secret -
Click Add.
-
Copy the Value of this new client secret by clicking on the Copy to clipboard icon next to it.
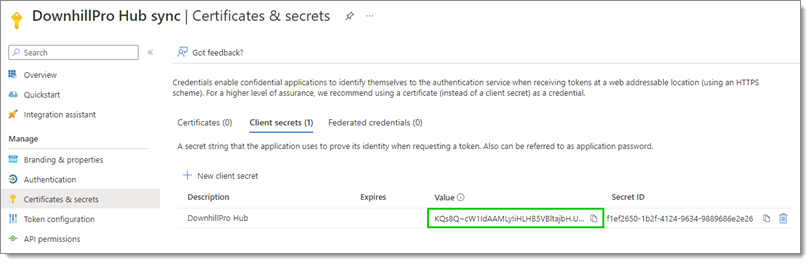
Copy the client secret value The expired client secret can be deleted without any issue since it is expired and cannot be used anymore.
-
Log in to Devolutions Hub Business using your Devolutions Account.
If you have enabled the Force SSO on all users option in your configuration, you will not be able to log in using your Devolutions Account. In this case, contact our customer support team to request the disabling of this option.
-
Once logged in, go to Administration – Authentication – Single Sign-On (SSO), then select your Microsoft SSO configuration.
-
Replace the currently expired Client secret key with the newly created one you copied earlier.
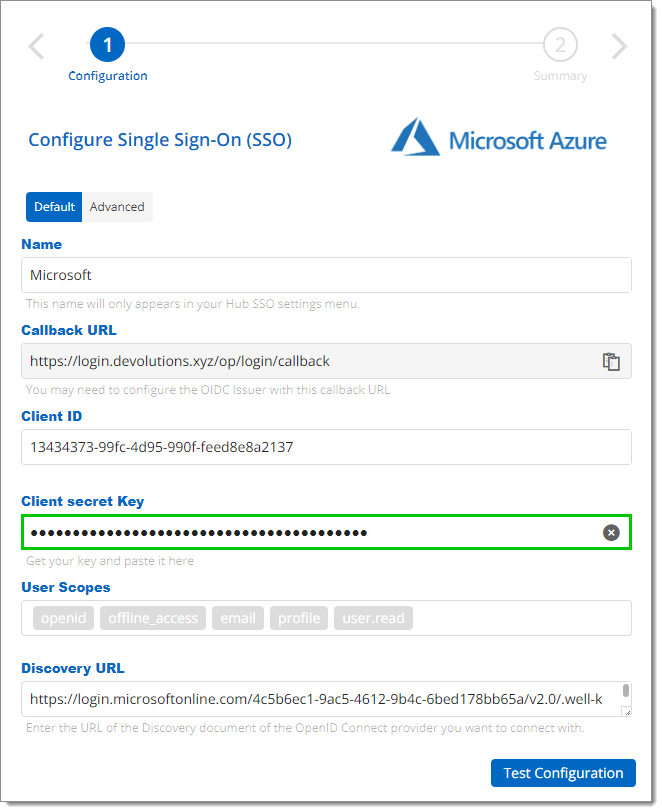
Replace the client secret key -
Click Test Configuration.
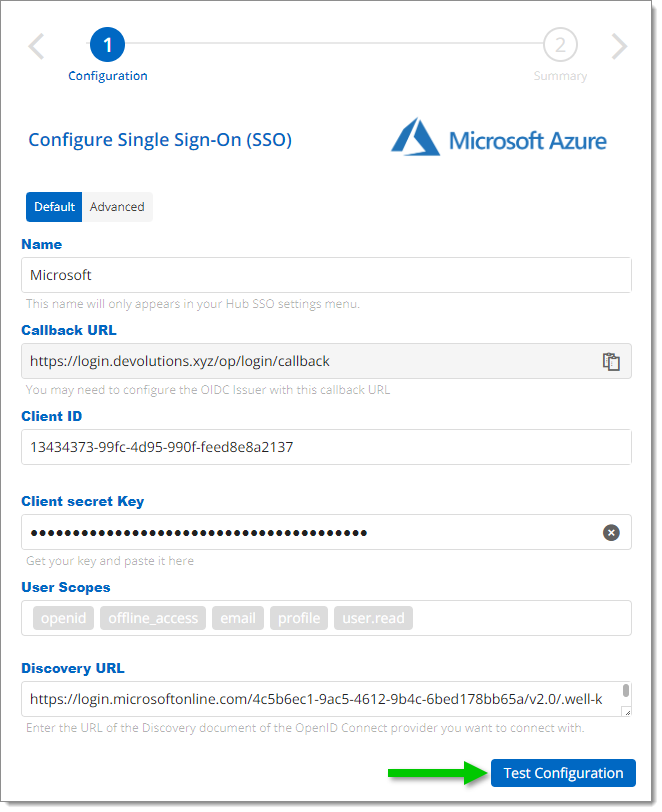
Test Configuration -
If the connection is successful, your account will connect with Entra ID (formerly Azure AD) and you will see a summary of your configuration.
-
In the Summary of your configuration, click Save.
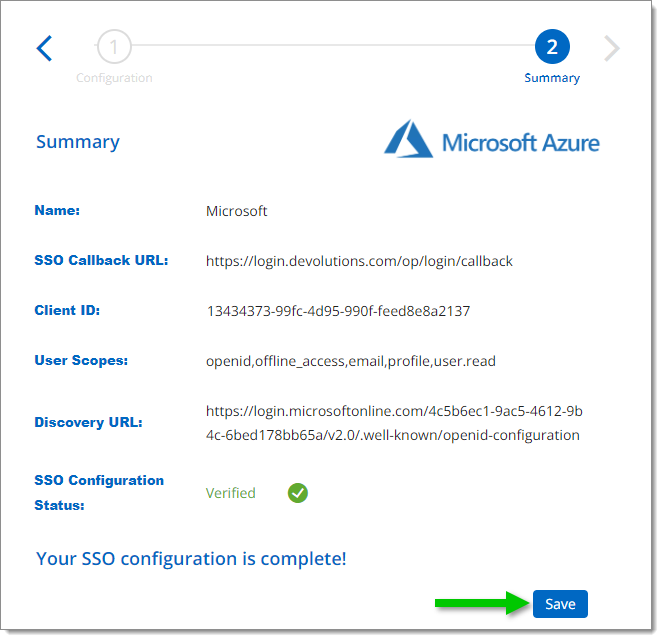
Save your configuration
You and your users should now be able to sign in to the hub using Microsoft SSO.
If you still encounter issues, contact our customer support team.