Rotating SSH key manually across large, complex environments can become unwieldy and raise security risks. We therefore recommend using Devolutions Server’s PAM features to centralize SSH key management.
This method is rather straightforward: SSH keys imported from an SSH key provider in Devolutions Server are linked to SSH entries in Remote Desktop Manager, allowing for simplified, centralized key management.
Devolutions PAM’s SSH key rotation requires access to authorized_keys files in your managed systems. It is therefore recommended to use the StrictModes configuration within your SSH server settings.
For StrictModes compatibility, use the following commands on filesystems supporting Access Control Lists (ACLs):
setfacl -m u:<PAM_USER>:--x /home/<ACCOUNT>
setfacl -m u:<PAM_USER>:--x /home/<ACCOUNT>/.ssh
setfacl -m u:<PAM_USER>:rw /home/<ACCOUNT>/.ssh/authorized_keys
Replace <PAM_USER> with the username of the account Devolutions PAM uses to manage SSH keys and switch ACCOUNT with all the accounts to be managed with SSH keys.
-
In Devolutions Server, go to Administration – Privileged access – Providers and click the Add (+) icon. Select the SSH key managed provider type.
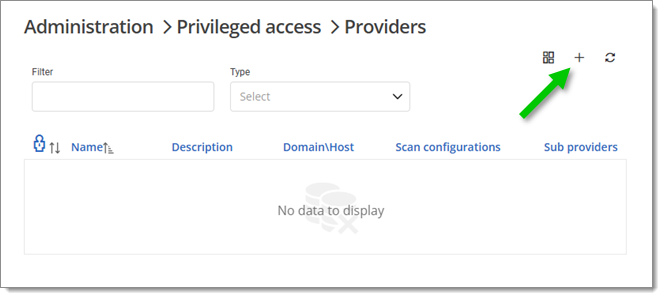
Add a provider -
Enter the required information. Be sure to check both Add PAM vault and Add a new account discovery configuration.
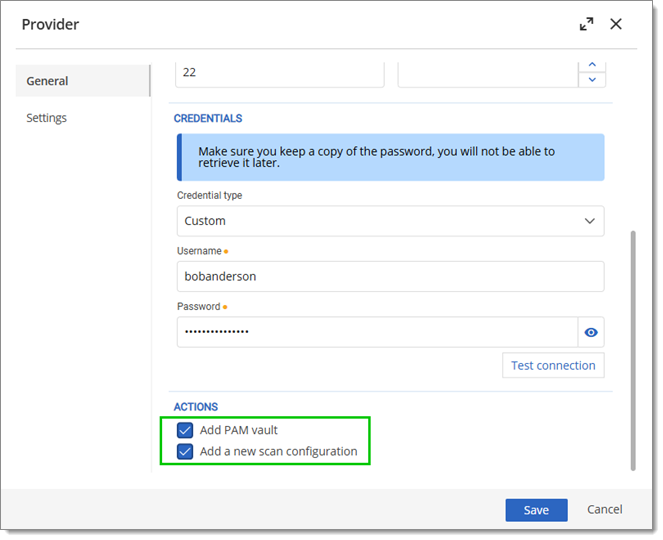
Enter credentials and check options to add PAM vault and account discovery configuration -
Click on Test connection to make sure everything is in order, and Save the provider.
-
Then, in the Account discovery configuration window, enter a name and click Ok.
-
Head over to Administration – Privileged access – Account discovery configurations. Click on the View result button (eye icon) of the newly created account discovery configuration.
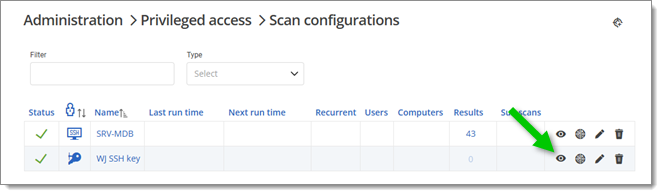
View result of configuration scan -
Select the SSH key you wish to use and click on the Import selected computers button.
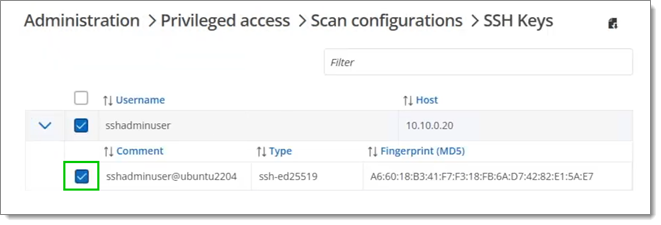
Select the key to import -
Set a destination folder for the imported key and click Ok.
-
Click Add a new entry and create an SSH terminal session entry. Enter host and credentials.
-
In the General sub-tab of the SSH key tab, set the Entry type to Privileged account. Click the ellipsis (…) icon right of the Account field and find your PAM account.
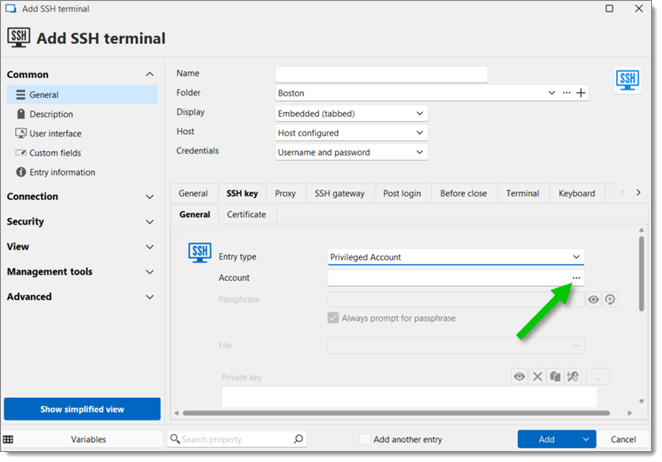
Select your PAM account -
Click Ok, and then Add to finalize entry creation.
To make sure the method worked, check out the SSH terminal entry in Remote Desktop Manager, and enter cat ~/.ssh/authorized_keys in the console. The key returned should then match the one in the PAM folder created during step #7 in Devolutions Server.