The following guide provides steps to create an Azure AD user PAM provider for Devolutions Server.
In the Azure Portal
- In a browser page, open the Microsoft Azure AD Portal and sign in to your account.
- Select Microsoft Entra ID in the Azure Services section. If you do not see it, click on More services to make other services appear.
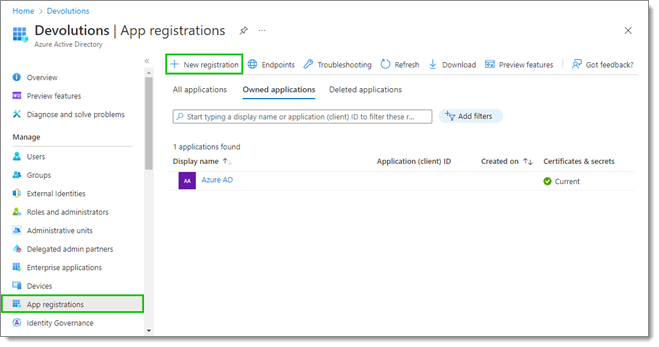
- In App registrations, click on New registration.
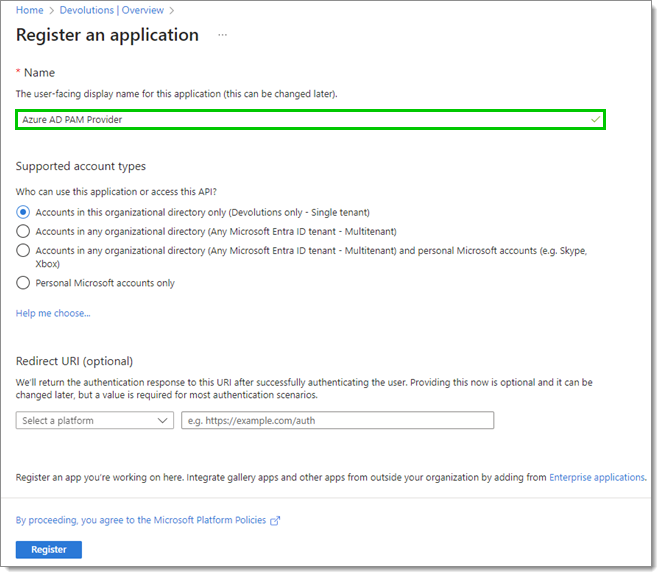
- Set the Name of your application.
- Click Register at the bottom when done.
In Devolutions Server
- Connect to your Devolutions Server.
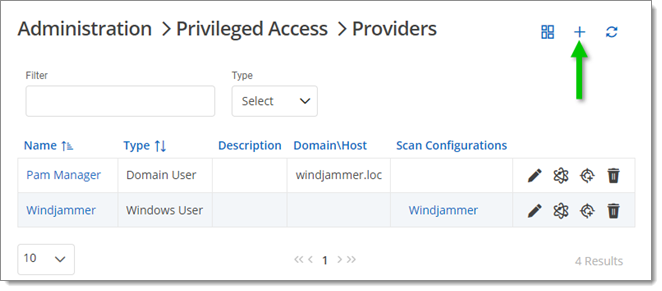
- Go to Administration – Privileged Access – Providers, then click on Add.
- Select Azure AD User as the new PAM provider, then click Continue.
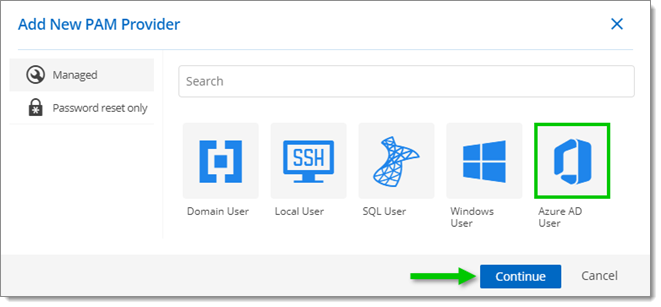
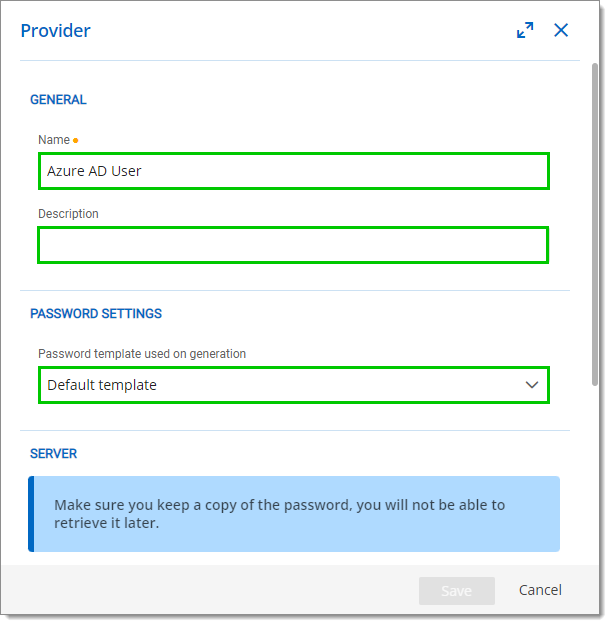
- In the Provider window, enter a Name (mandatory) and a Description (optional) for your new Azure AD User PAM Provider. If need be, select a Password template in the drop-down list.
In the Azure Portal
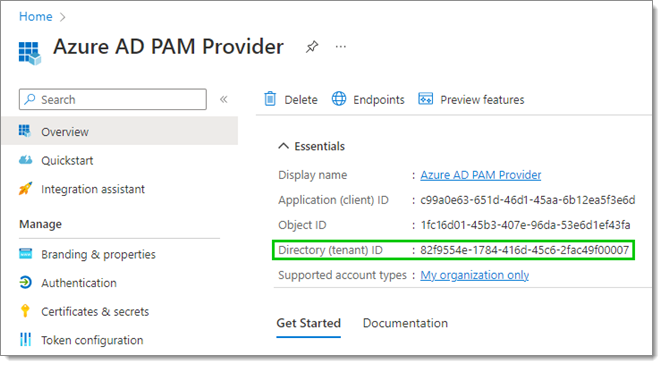
- In the Overview of your new app registration, copy the Directory (tenant) ID.
In Devolutions Server
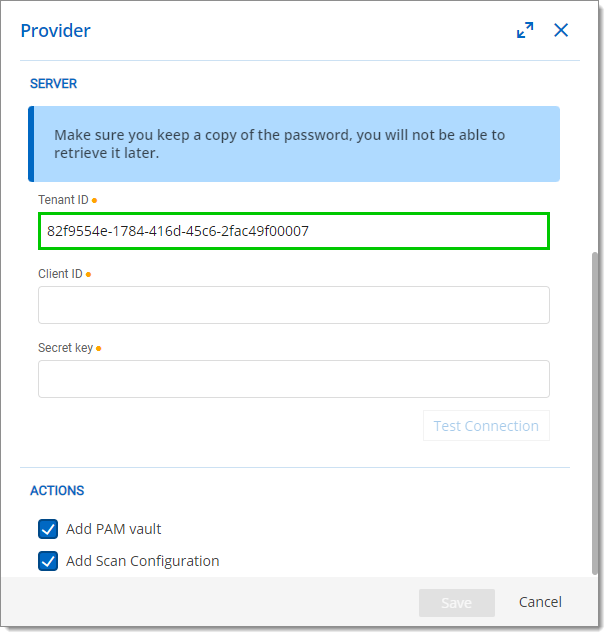
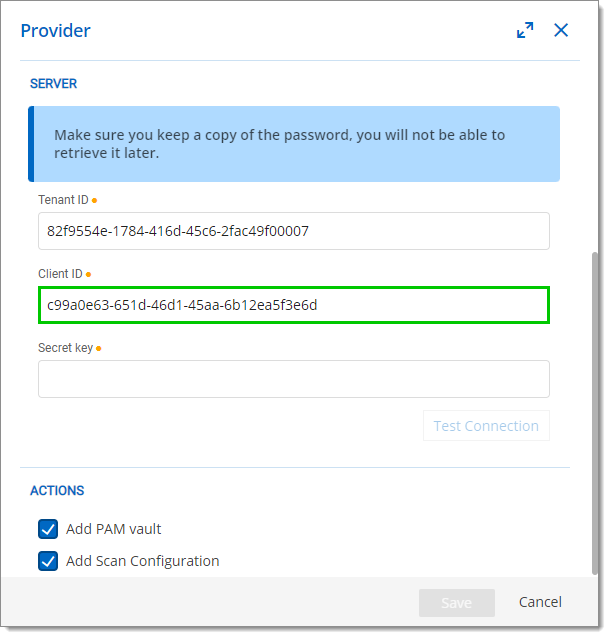
- Paste the ID copied in the previous step in the Tenant ID field.
In the Azure Portal
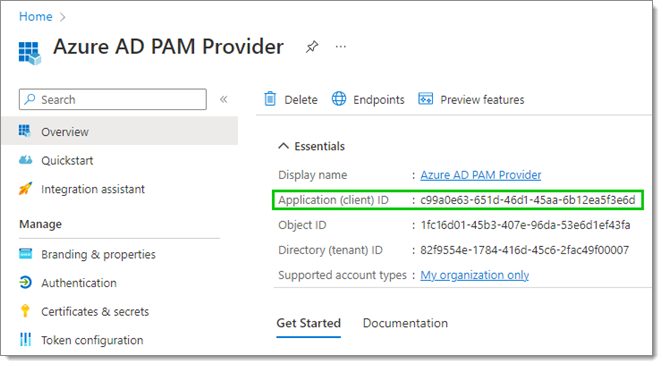
- Still in the Overview of your new app registration, copy the Application (client) ID.
In Devolutions Server
- Paste the ID copied in the previous step in the Client ID field.
In the Azure Portal
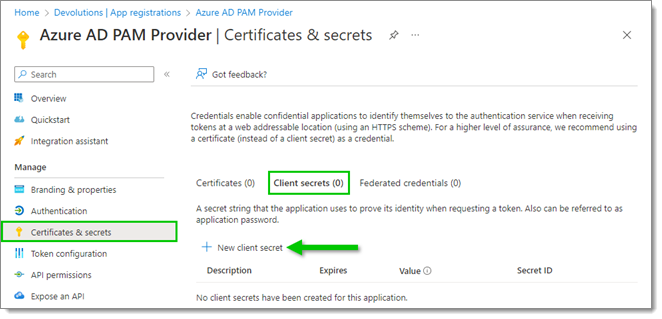
- In Certificates & secrets, click on Client secrets, then on New client secret.
- In the Add a client secret window, enter a Description and select an expiration date for this client secret, as per your best internal security practices.
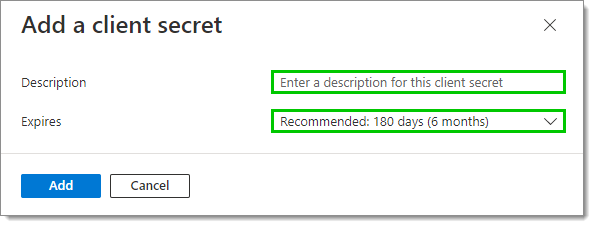
- Click Add.
- Copy the Value of this new client secret by clicking on the Copy to clipboard icon next to it.
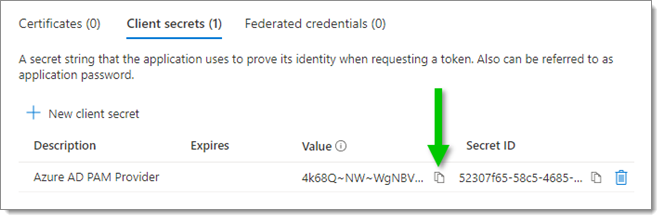
In Devolutions Server
- Paste the value copied in the previous step in the Secret key field.
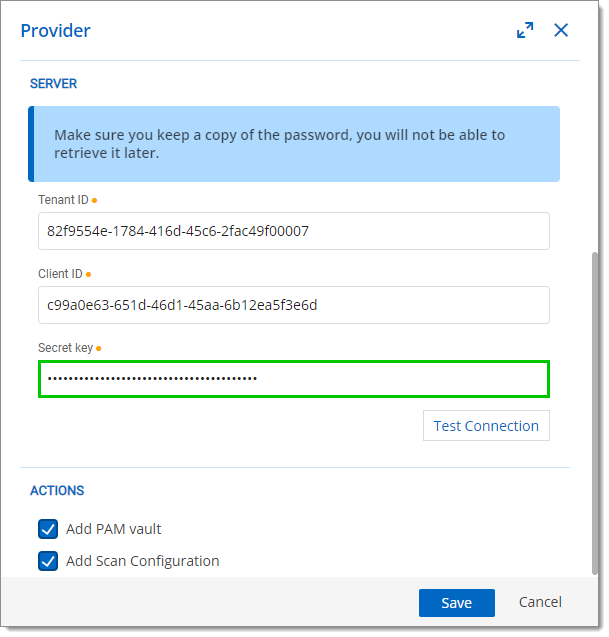
- Test the connection to see if it works, then click Save. The Scan Configuration window will appear: keep it open as it will be filled in a later step.
In the Azure Portal
Assigning API permissions as described in steps 20 to 26 is only useful if you want to perform Azure accounts discovery (scan). If this is not the case, to avoid assigning unnecessary permissions to the application, skip to step 27.
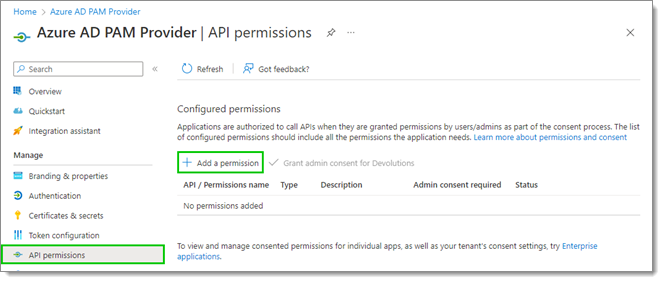
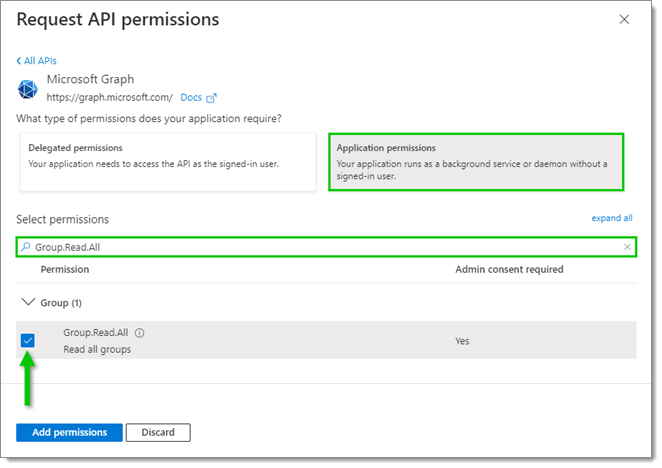
- In API permissions, click Add a permission.
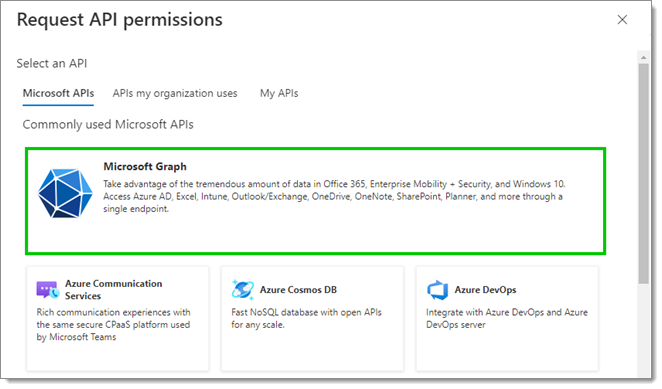
- In the Resquest API permissions window, select Microsoft Graph.
-
Click Application permissions, then check the boxes next to the following Microsoft Graph API permissions to select them:
- Group.Read.All
- RoleManagement.Readwrite.Directory
- User.Read.All
Select API permissions
Use the filter bar above the permissions list to find the ones you are looking for.
- When all the above permissions have been selected, click Add permissions at the bottom.
- The list of permissions will be updated to include those just selected. Remove any other unnecessary permissions using the ellipsis button next to them.
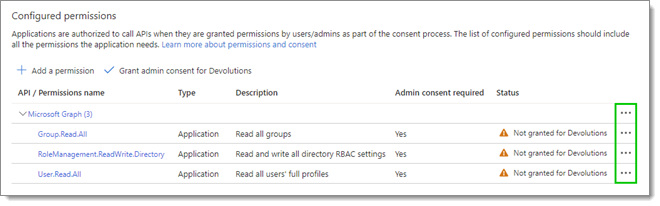
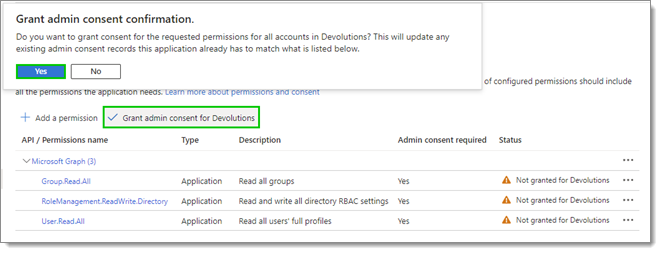
- The permissions require admin consent. Click on the Grant admin consent for < Your Organization > button, then click Yes to confirm.
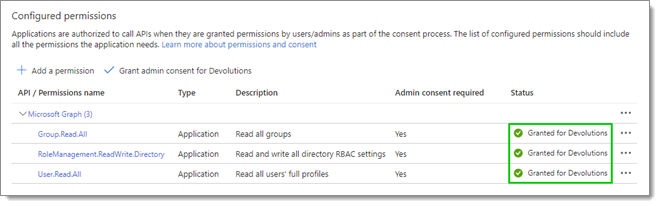
- To confirm that the admin consent has been granted, check the Status of your permissions.
- To grant the application the ability to rotate passwords, leave the App registrations to go back to Azure Active Directory, then select Roles and administrators in the left menu.
- In All roles, click on the Helpdesk Administrator role. If the accounts managed by the PAM module are members of any administrator roles or group –or if Privileged Identity Management (PIM) is used–, then the application needs the Privileged Authentication Administrator role.
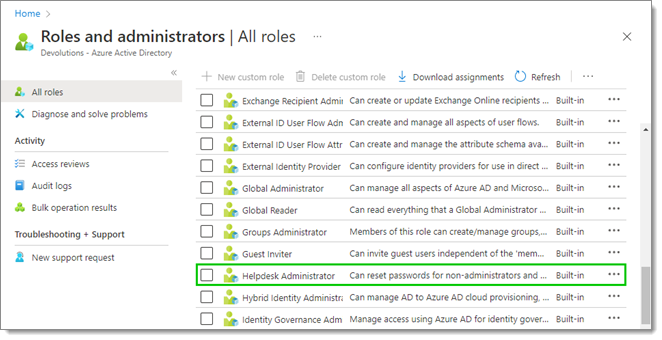
- In Assignments, click on the Add assignments button.
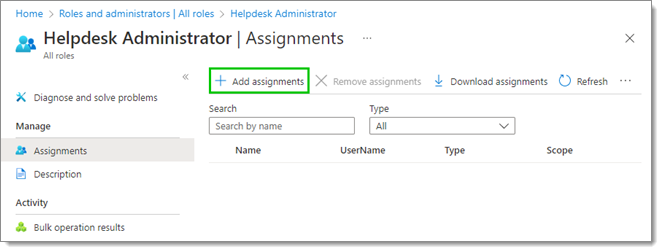
- Filter the list to find the Azure application previously created, select it, then click Add.
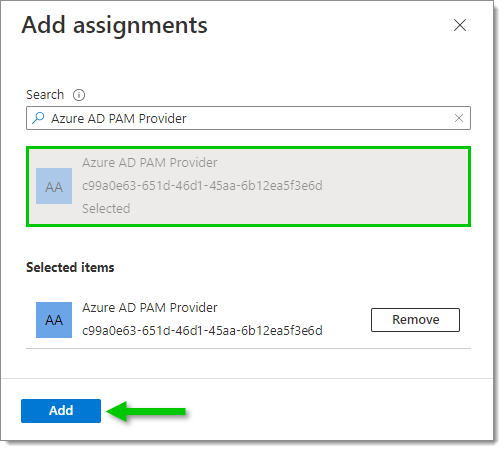
Your new assignment should now be displayed in Assignments.
In Devolutions Server
- The last steps are dedicated to configuring a scan for this provider. In the Scan Configuration window that appeared when you saved your provider configuration in step 19, under General, enter a Name for this configuration.
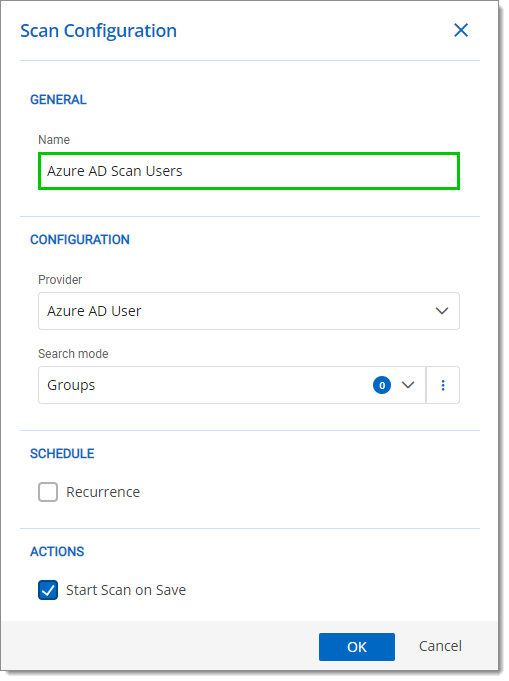
- Under Configuration, select Groups or Roles in the Search mode drop-down list. You can filter the Search mode for specific Azure AD groups or roles by clicking on the Edit button next to the drop-down list.
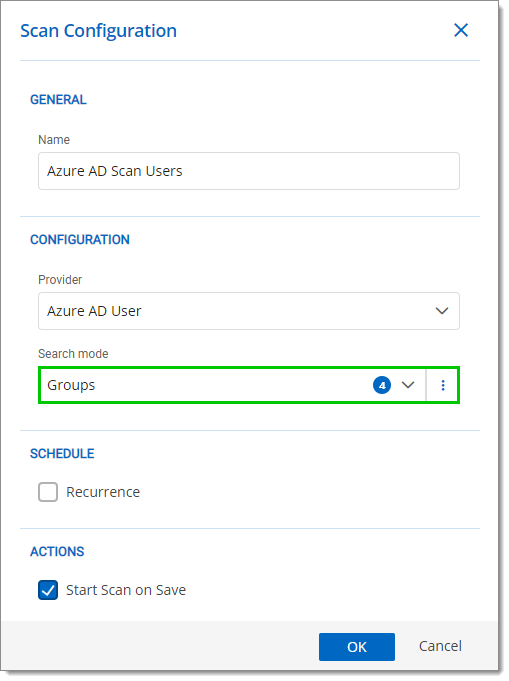
- Click OK when the configuration is done.
- In Devolutions Server, go to Administration – Privileged Access – Scan Configurations. If the Start Scan on Save option was left enabled during the scan configuration, the scan should have started by itself. During the process, the Status column displays an hourglass icon next to the scan entry.
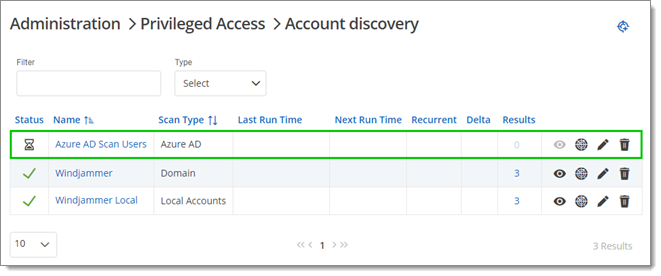
- When the process is complete, the hourglass icon changes to a green check mark. At that point, select accounts and import them into the privileged accounts like any other type of privileged account.







