Integrating an AWS IAM provider with Devolutions Server allows you to centralize identity and access management by leveraging your existing AWS credentials. This configuration enables account discovery, heartbeat monitoring, and password rotation for your AWS resources.
-
Create a user in AWS who will act as a provider.
-
Create an access key.
-
The following permissions are required for the AWS identity provider:
Please refer to the AWS Identity and Access Management documentation for more details on each action.
ACTION | DESCRIPTION |
|---|---|
| To ensure the necessary permissions are in place before proceeding. |
| To ensure the necessary permissions are in place before proceeding. |
ACTION | DESCRIPTION |
|---|---|
| To get a list of access keys. |
| To get a list of IAM users. |
ACTION | DESCRIPTION |
|---|---|
| To check whether a login profile needs to be created or updated. |
| To generate a password if non exists. |
| To update the password. |
ACTION | DESCRIPTION |
|---|---|
| To generate an access key on import or rotation. |
| To delete the previous access key after rotation. |
| To disable the previous access key before deletion. |
| To verify if we need to update the tag of an access key |
| To add a tag to the user in the format |
| To remove an existing access key tag. |
Here is the full .JSON policy for the AWS console. It can be used on a user or a group.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"iam:SimulatePrincipalPolicy",
"iam:GetUser",
"iam:ListUsers",
"iam:ListAccessKeys",
"iam:GetLoginProfile",
"iam:CreateLoginProfile",
"iam:UpdateLoginProfile",
"iam:CreateAccessKey",
"iam:DeleteAccessKey",
"iam:UpdateAccessKey",
"iam:ListUserTags",
"iam:TagUser",
"iam:UntagUser"
],
"Resource": "*"
}
]
}
-
To create the AWS IAM user provider in Devolutions Server, go to Administration – Privileged access – Providers and click Add.
-
Click AWS IAM User under Managed.
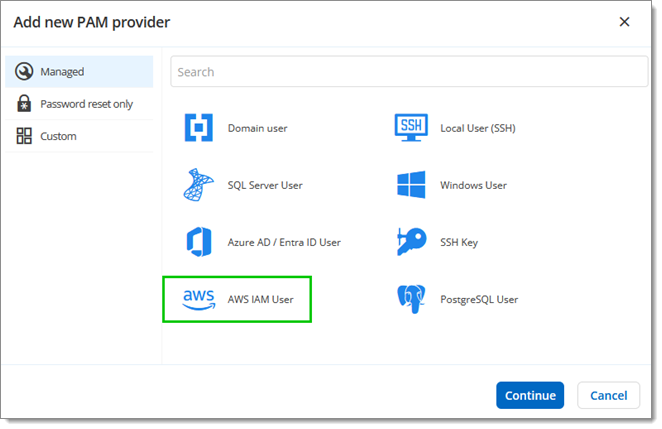
Click AWS IAM User -
Enter a name and a description.
-
Under Credential type, select Custom or Linked credential.
-
If Custom is selected, enter the access key and the secret key from AWS.
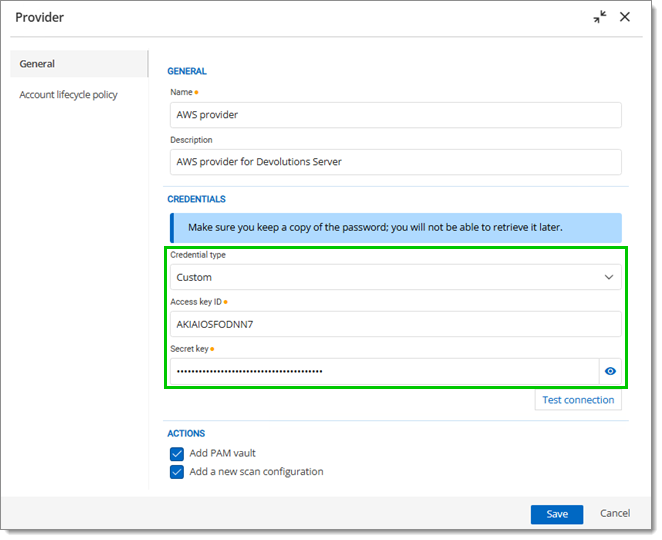
Custom type credential -
If Linked credential is selected, choose the privileged account in the drop-down menu.
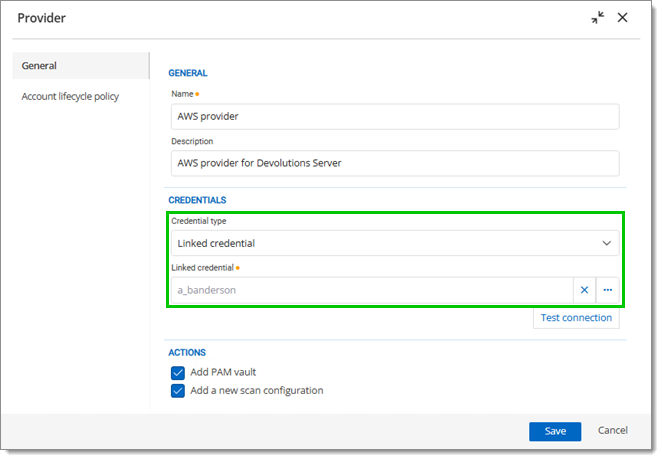
Linked credential -
Check Add PAM vault or Add a new account discovery configuration if needed.
To do a reset password on import, a password policy must be created that follows the AWS default password policy.
-
Go to the Account lifecycle policy tab.
-
Select the password policy previously created.
-
Click Save to close the window.