Installing and running Devolutions Gateway on Linux is quick and easy, provided several prerequisites are met. Ubuntu 22.04 LTS was used to demonstrate the installation and configuration.
Devolutions Server or Devolutions Hub Business is needed for the configuration as well as a Devolutions Gateway license.
Install Devolutions Gateway
-
Navigate to the Devolutions Gateway GitHub Release page and download the .deb file of the latest release.
-
Input the following using the command-line:
wget https://github.com/Devolutions/devolutions-gateway/releases/download/v2024.3.2/devolutions-gateway_2024.3.2.0_amd64.deb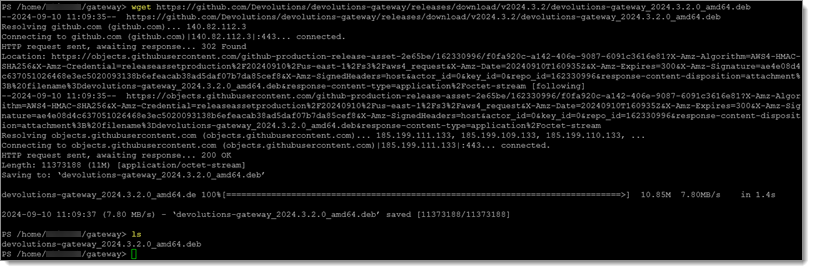
Command-line wget -
Install the package using the
dpkgutility:sudo dpkg -i devolutions-gateway_2024.3.2.0_amd64.deb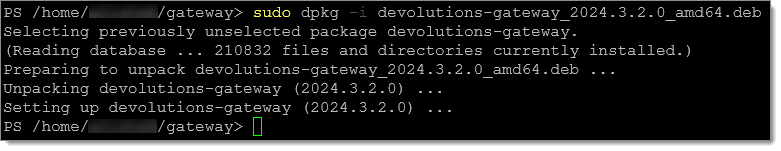
Command-line dpkg
The configuration and binary packages are in the following locations:
Configuration:
/etc/devolutions-gatewayBinary:
/usr/bin/devolutions-gateway
Update Devolutions Gateway
To update Devolutions Gateway on Linux download the latest package as explained in the previous section and run the installation command. The package will install over the existing installation and preserve configurations.
Install the PowerShell gateway module
It is recommended to use the PowerShell gateway module to configure and manage the Devolutions Gateway instance on Linux.
-
Install PowerShell with this command:
source /etc/os-release wget -q https://packages.microsoft.com/config/ubuntu/$VERSION_ID/packages-microsoft-prod.deb sudo dpkg -i packages-microsoft-prod.deb rm packages-microsoft-prod.deb sudo apt-get update sudo apt-get install -y powershell -
Install the Devolutions Gateway PowerShell module:
Install-Module -Name DevolutionsGateway Import-Module -Name DevolutionsGateway
Once installed the Devolutions Gateway configuration can be started, stopped, viewed or modified.
Configure certificates
Proper trust of certificates between systems is key to making Devolutions Gateway work. Functionality such as websockets used in web dashboard views of RDP, SSH, etc., requires a properly trusted certificate. A certificate generated on the Linux system and trusted by computers used to connect is needed.
Generate a self-signed certificate on Ubuntu 22.04 LTS via OpenSSL
Using the OpenSSL utility, generate a certificate directly from the command line. The certificate then needs to be placed directly into the configuration directory /etc/devolutions-gateway.
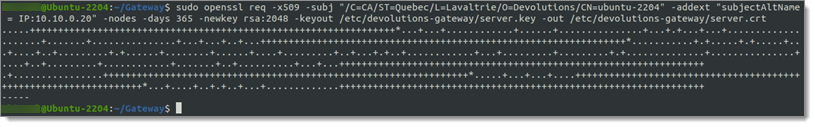
sudo openssl req -x509 -subj "/C=CA/ST=Quebec/L=Lavaltrie/O=Devolutions/CN=ubuntu-2204" -addext "subjectAltName = IP:10.10.0.20" -nodes -days 365 -newkey rsa:2048 -keyout /etc/devolutions-gateway/server.key -out /etc/devolutions-gateway/server.crt
The certificate request will look different for every configuration.
Customization options | Explanation |
|---|---|
| Create and process certificate requests including self-signed certificates in PKCS#10 format. |
| Output a self-signed certificate. |
| Define the certificate subject on the command-line. There must be no spaces between sections.
|
| To add a Subject Alternate Name (SAN), you can use this parameter to define either an IP or DNS entry.
|
| Do not encrypt the created private key. |
| The number of days the certificate is valid. |
| Define the algorithm and bit size, here |
| The location to create the private key file. |
| The location to create the public key file. |
Trust the self-signed certificate on Ubuntu
Once the self-signed certificate is created the certificate within the Ubuntu system will need to be trusted. To trust system-wide use the following set of commands:
cd /etc/devolutions-gateway
sudo apt-get install -y ca-certificates
sudo cp server.crt /usr/local/share/ca-certificates
sudo update-ca-certificate
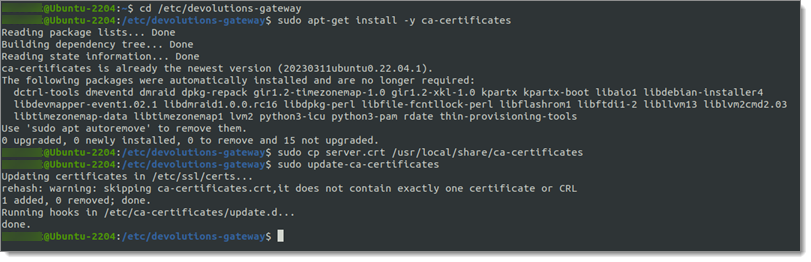
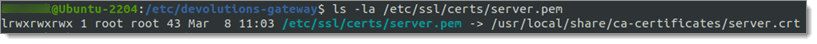
The ca-certificates may already be installed. By running the update-ca-certificates command a symlink will be created in /etc/ssl/certs to the copied certificate file in /usr/local/share/ca-certificates.
If this is done in Firefox multiple trust errors will appear as the browser does not use the system-wide certificate store. Their documentation offers a few solutions to this.
Trust the self-signed certificate on Windows
After the self-signed certificate is created it will need to be trusted on Devolutions Server. The server.crt and server.key files will need to be transferred to the Windows system; or copy and paste the contents into files (i.e. sudo cat server.crt in Ubuntu and copy that into a text file on Windows).
-
Copy the public key to Windows (in the example, C:\Gateway is a temporary location):
sudo cat server.crt
Command-line sudo cat server -
Copy the content into a server.crt file.
Server.crt file -
Copy private key to Windows:
sudo cat server.key
Copying the key to Windows -
Copy the content into a server.key file.
Server.key file -
Create a PFX file using the Windows certutil command-line tool. For this to work, the key file must be named the same as the crt file, only differing in extension:
certutil -mergepfx server.crt server.pfx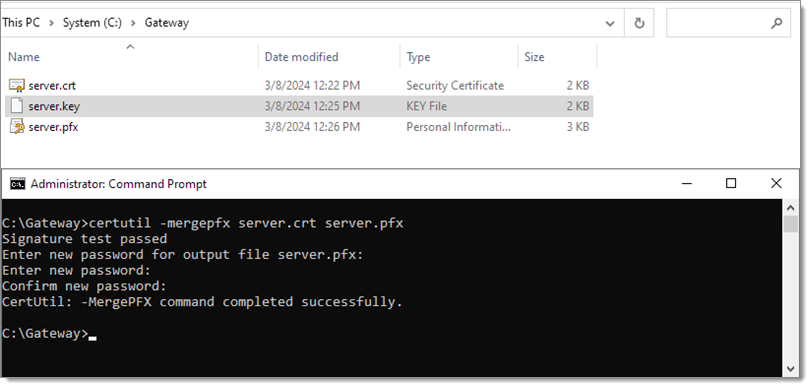
Create a PFX file -
Import the PFX file into the Trusted Root Certification Authorities Certificate Store.
-
Double-click the server.pfx file to start the import wizard and choose Local Machine.
-
Click Next and accept the prompt.
Click Next -
Click Next.
Click Next -
Enter the password that you entered with the
certutilcommand.- Optionally: choose to Mark this key as exportable.
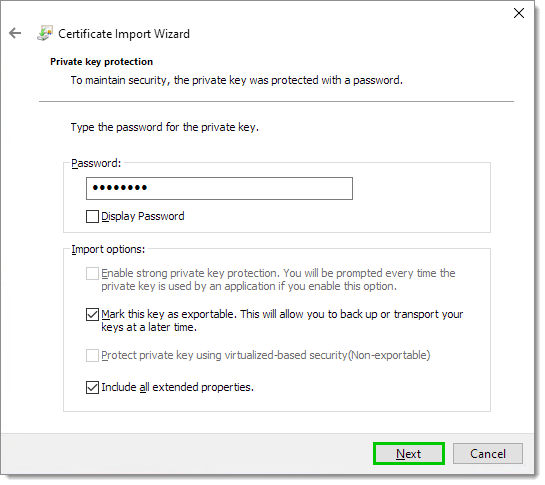
Enter the password -
Choose the option Place all certificates in the following store.
-
Select Trusted Root Certification Authorities with the Browse... button.
-
Click Next.
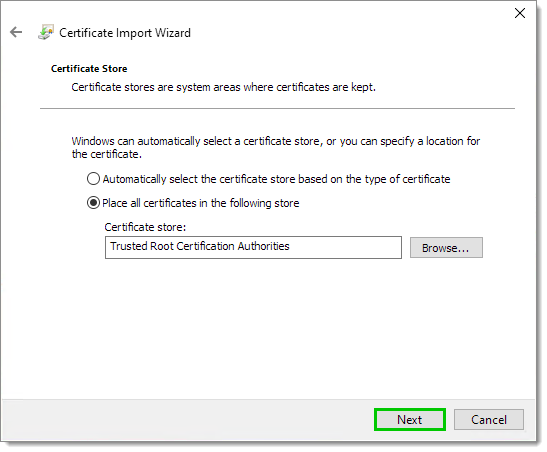
Click Next -
Click Finish to complete the import.
-
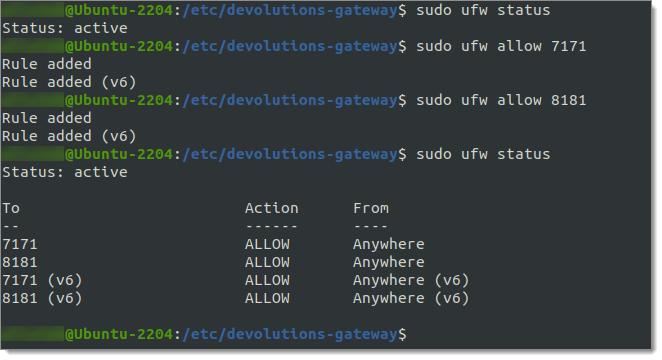
Open Ubuntu firewall ports
If the Linux system uses UFW (Uncomplicated Firewall) to manage iptable-based firewall, perform the following commands to open the necessary ports:
sudo ufw status
sudo ufw allow 7171
sudo ufw allow 8181
sudo ufw status
Modify the Devolutions Gateway configuration
The default configuration of a gateway contained in the /etc/devolutions-gateway/gateway.json file needs the certificate directives added (the InternalUrl will need to use HTTPS):
{
"Id": "YOUR-UNIQUE-GUID",
"ProvisionerPublicKeyFile": "provisioner.pem",
"ProvisionerPrivateKeyFile": null,
"Listeners": [
{
"InternalUrl": "tcp://:8181",
"ExternalUrl": "tcp://:8181"
},
{
"InternalUrl": "http://:7171",
"ExternalUrl": "https://:7171"
}
]
}
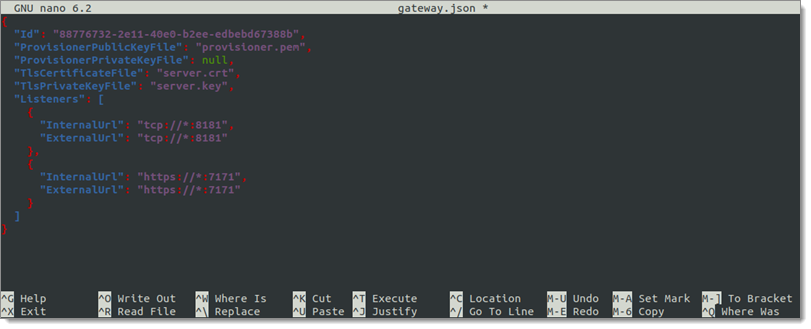
Modify the above file to reflect the following, assuming that both server.crt and server.key are in the same directory as gateway.json (using the built-in file editor Nano is recommended):
{
"Id": "YOUR-UNIQUE-GUID",
"ProvisionerPublicKeyFile": "provisioner.pem",
"ProvisionerPrivateKeyFile": null,
"TlsCertificateFile": "server.crt",
"TlsPrivateKeyFile": "server.key",
"Listeners": [
{
"InternalUrl": "tcp://:8181",
"ExternalUrl": "tcp://:8181"
},
{
"InternalUrl": "https://:7171",
"ExternalUrl": "https://:7171"
}
]
}
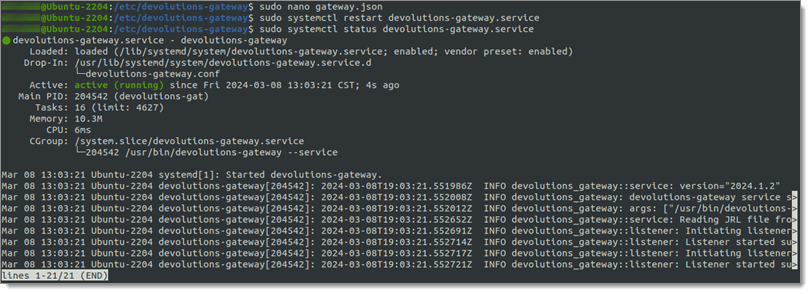
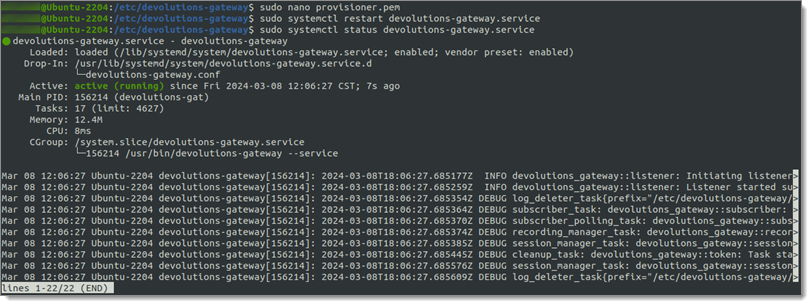
Restart Devolutions Gateway
With the new configuration in place restart Devolutions Gateway. This can be done with the systemctl command:
sudo systemctl restart devolutions-gateway.service
sudo systemctl status devolutions-gateway.service
Alternatively the Stop-DGateway and Start-DGateway PowerShell commands can also be used.
Connect Devolutions Gateway to Devolutions Server
Copy the Public Key from Devolutions Server to Devolutions Gateway Linux
-
Log into the Devolutions Server web console and navigate to Administration – Devolutions Gateway.
-
Click the More button and choose the Download public key option.
Download public key -
Copy the contents of the downloaded gateway_public_key.pem file on Windows.
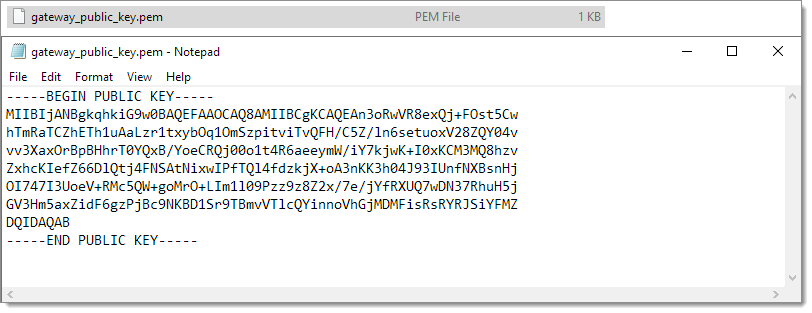
Copy the contents -
Replace the contents of the /etc/devolutions-gateway/provisioner.pem (the Nano utility is recommended) file with the copied contents from Windows.
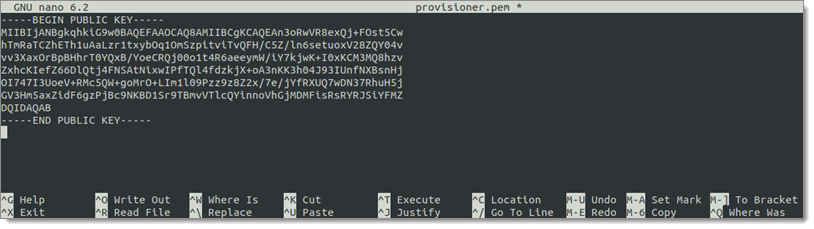
Replace the contents -
Restart Devolutions Gateway with the command
sudo systemctl restart devolutions-gateway.service.
Restart Devolutions Gateway
Configure Devolutions Gateway in Devolutions Server
Go to the Devolutions Server web interface where the newly configured Linux Devolutions Gateway will be added.
Before creating the Gateway configuration add the necessary license information in Administration – Licenses. Assign the license as needed during the configuration.
-
Log into the Devolutions Server web console and navigate to Administration – Devolutions Gateway.
-
Click the Add (+) button.
-
Select Gateway.
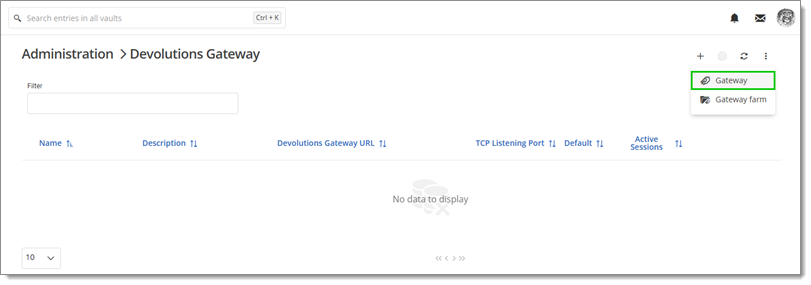
Select Gateway -
Enter the following (this will change depending on the configuration).
- Name: Linux Gateway
- Devolutions Gateway URL:
https://10.10.0.20:7171 - TCP Hostname:
Ubuntu-2204
-
Click Save.
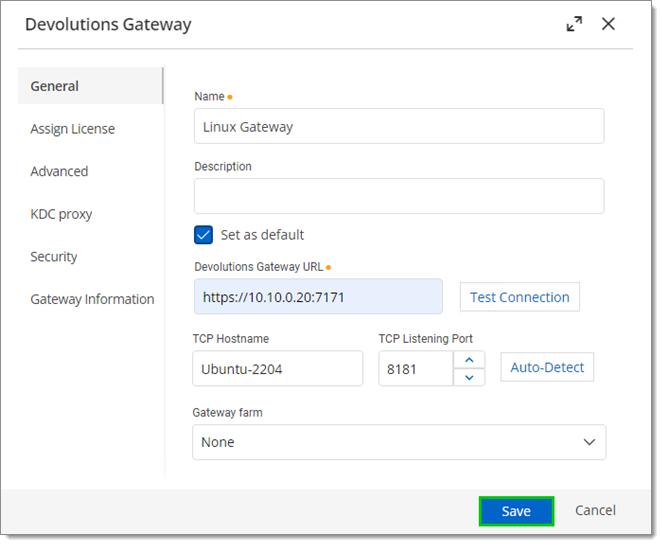
Click Save
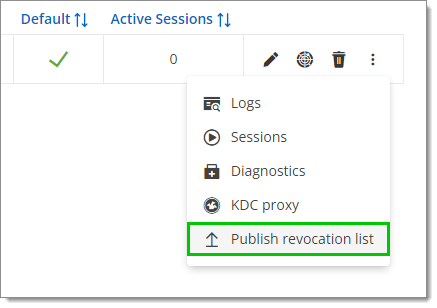
Click the More options menu for the gateway and choose the Publish revocation list option if the revocation list is out of date.
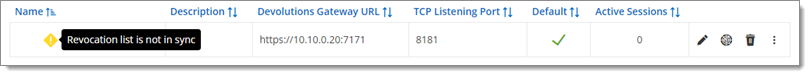
Resolve hosts in Ubuntu
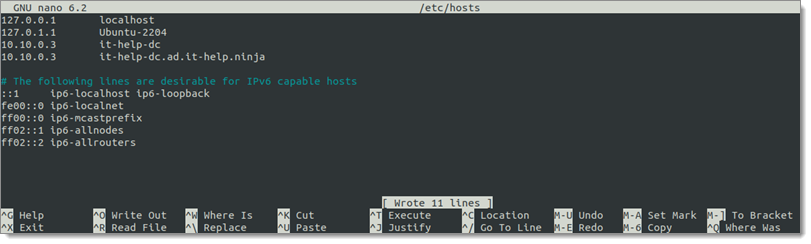
The Linux-hosted Devolutions Gateway system must be able to resolve the addresses that are requested by Devolutions Server. The simplest method for testing is to modify the hosts file.
Connect to the following system:
- Hostname:
it-help-dc - Fully-Qualified Domain Name (FQDN):
it-help-dc.ad.it-help.ninja - IP Address:
10.10.0.3
Open the hosts file for editing sudo nano /etc/hosts to add the host in Ubuntu.
Open a web-based RDP session
The gateway can now to connect to hosts. Since the it-help-dc host was added as resolvable to Ubuntu it can be used to connect in a web-based session.
Web-based sessions require an active gateway configured for the entry and the user launching will require an assigned Remote Desktop Manager Team edition license or Devolutions Launcher license.
Additionally, if changes have been made to license assignments, logging out and back in may be needed to see the option to launch the web-based connection.
-
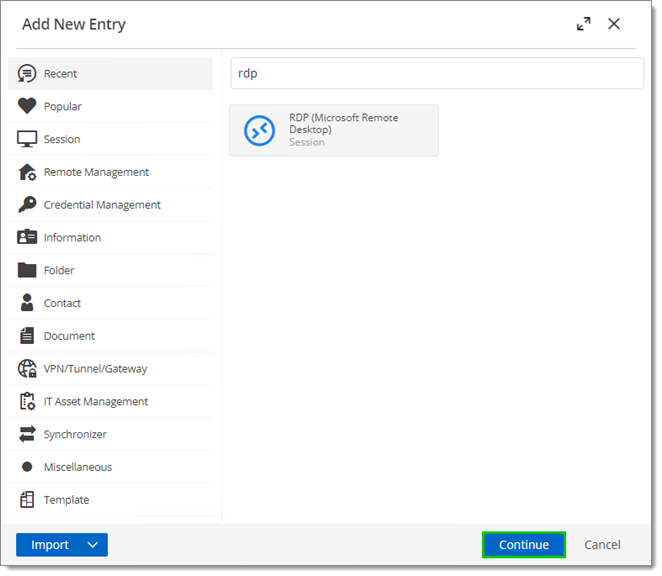
In the Devolutions Server web UI click on Add. Select an RDP session entry.
-
Click Continue.
Click Continue -
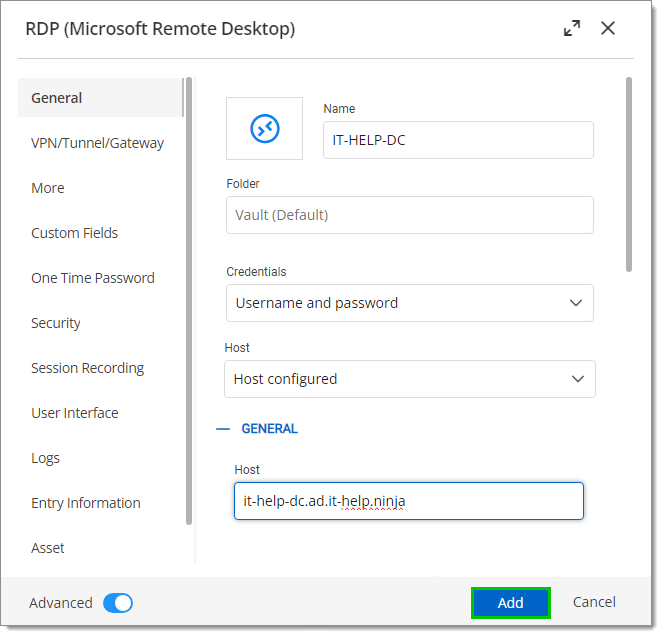
Enter a Name and Host which must be resolvable by the Linux Devolutions Gateway install.
-
Click Add.
Click Add -
Enter or link any necessary credentials to the RDP session and click Add.
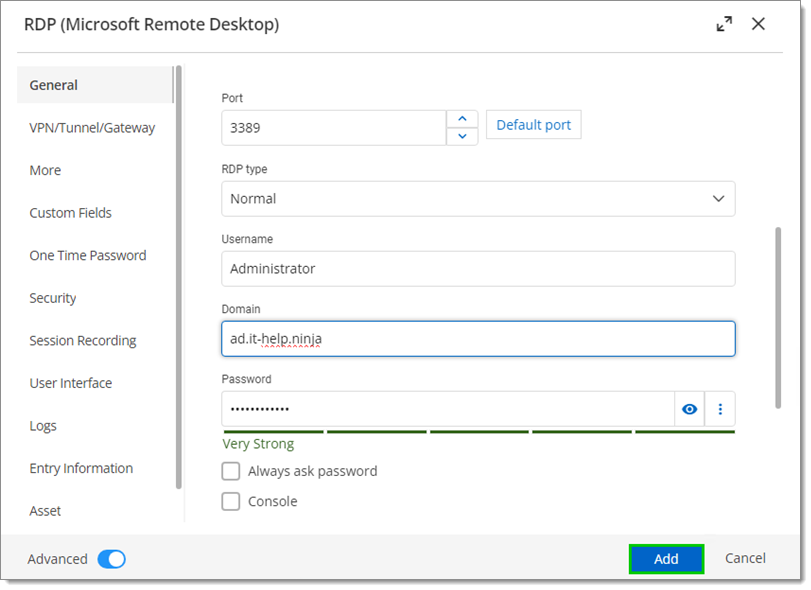
Enter or link credentials -
Under the VPN/Tunnel/Gateway tab choose Devolutions Gateway as the VPN type.
-
Set the Connect option to Always connect.
-
Choose the correct gateway.
-
Click Add.
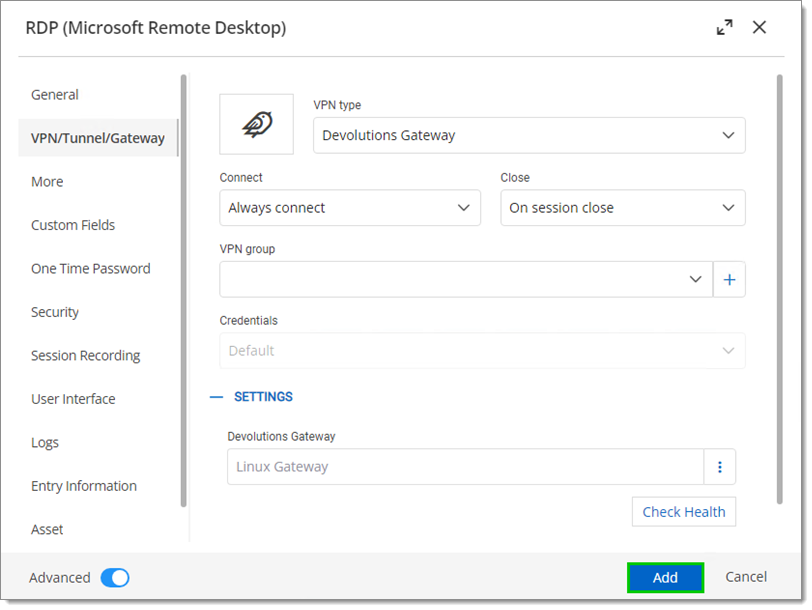
Choose the correct gateway -
Click Open in web client.
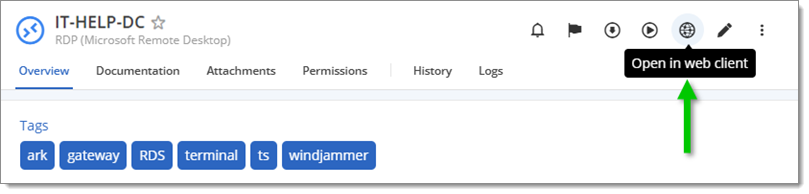
Open in web client
Open a Remote Desktop Manager RDP session
If the entry is already configured from within the Devolutions Server web interface it can be launched from Remote Desktop Manager when connected to the Devolutions Server data source.
When creating a new entry from Remote Desktop Manager the process is similar to that of Devolutions Server.
-
In Remote Desktop Manager click on New entry. Select an RDP session entry.
-
Click on Select.
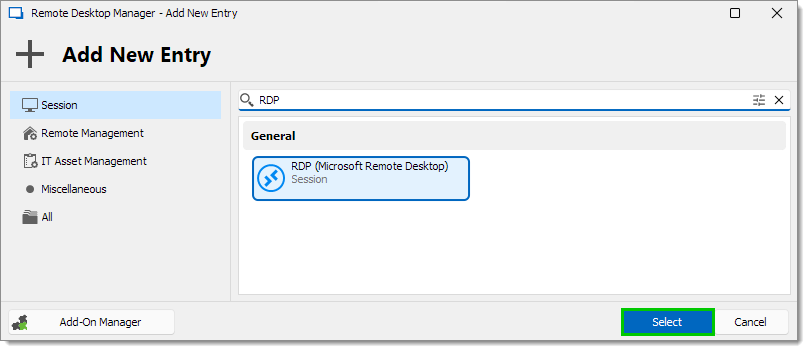
Click on Select -
Enter a Name and Host which must be resolvable by the Linux Devolutions Gateway install.
-
Enter or link any necessary credentials to the RDP session.
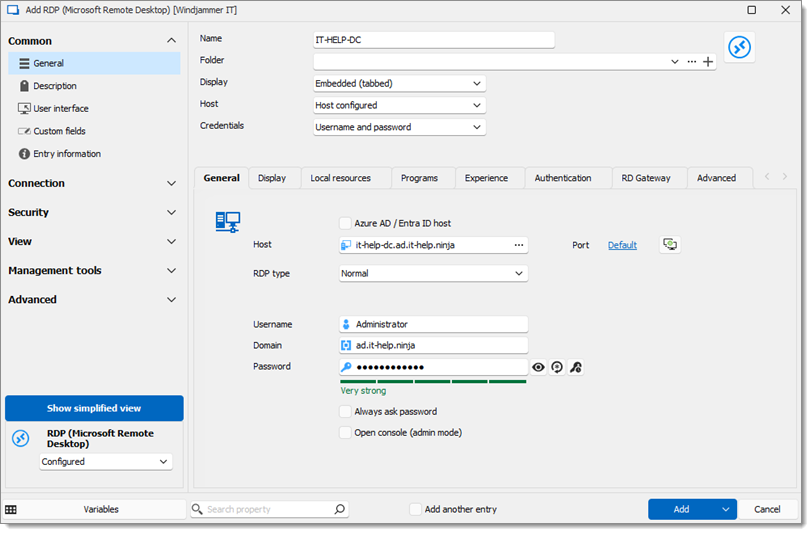
Fill in the necessary fields -
Set the Connect option to Always connect.
-
Under the VPN/Tunnel/Gateway tab choose Devolutions Gateway as the VPN type.
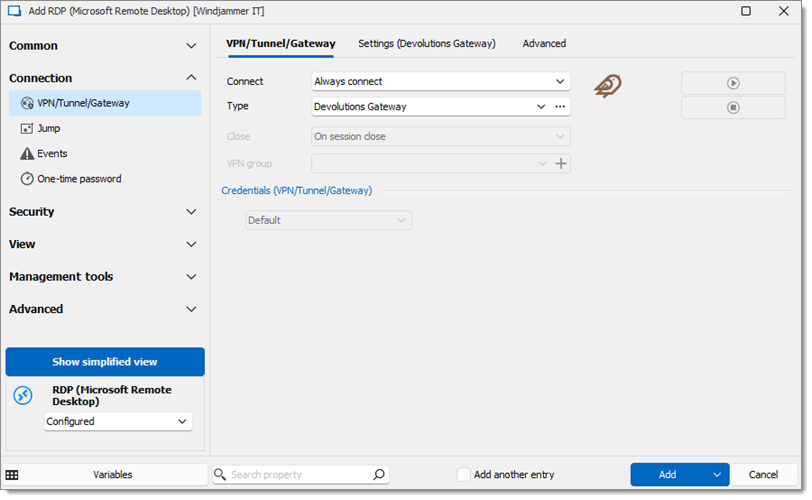
Adjust the General settings -
Go to the Settings (Devolutions Gateway) sub-tab.
-
Choose the desired Devolutions Gateway.
-
Click Add.
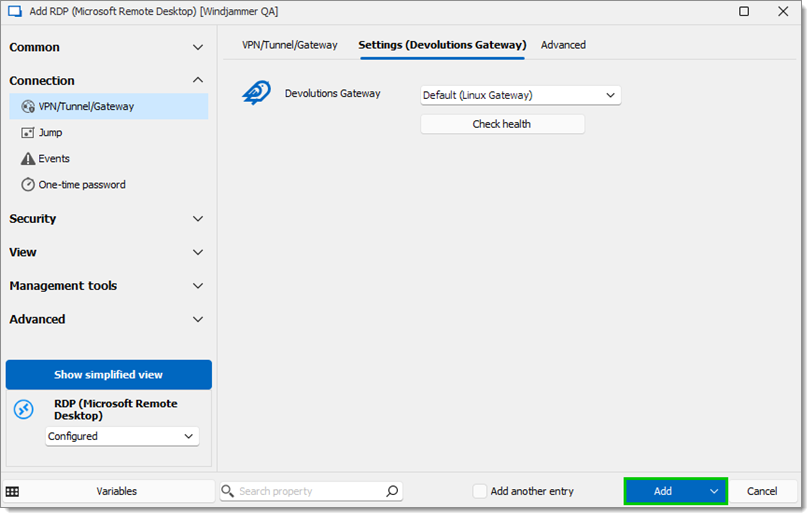
Click Add -
Click on the Open session button.
By hovering over the title bar a tooltip will appear and show that the RDP is connected via Devolutions Gateway.
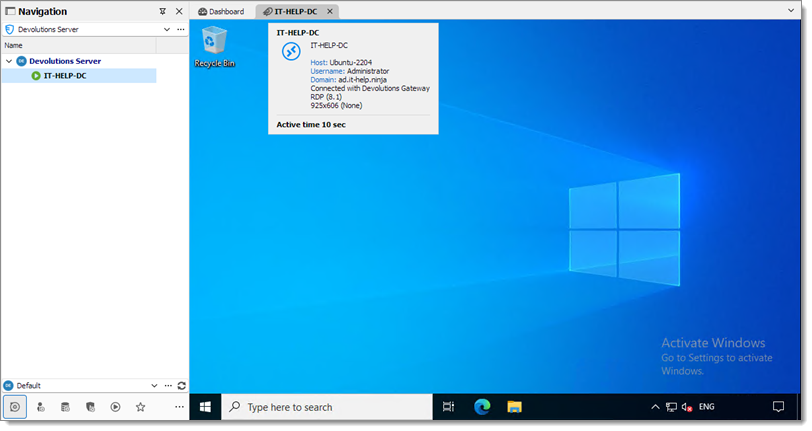
Enable Devolutions Gateway web interface
From version 2024.1.0 and onwards, a new Devolutions Gateway web interface was added. Modify the gateway.json to add the following section on WebApp using a utility such as sudo nano /etc/devolutions-gateway/gateway.json.
Previously the ProvisionerPrivateKeyFile was defined as null. When enabling the web application the file must be copied from Devolutions Server to a file accessible to Devolutions Gateway. As noted in the previous section, perform the same procedure but download the private key instead and transfer it to the Ubuntu system.
{
"Id": "YOUR-UNIQUE-GUID",
"ProvisionerPublicKeyFile": "provisioner.pem",
"ProvisionerPrivateKeyFile": "provisioner.key",
"TlsCertificateFile": "server.crt",
"TlsPrivateKeyFile": "server.key",
"Listeners": [
{
"InternalUrl": "tcp://:8181",
"ExternalUrl": "tcp://:8181"
},
{
"InternalUrl": "https://:7171",
"ExternalUrl": "https://:7171"
}
],
"WebApp": {
"Enabled": true,
"Authentication": "None"
}
}
Once modified restart the gateway:
sudo systemctl restart devolutions-gateway.service