Remote connection to systems using Kerberos tokens is a challenge without direct line of sight. A Kerberos KDC (Key Distribution Controller) proxy offers a method for a client to communicate with an intermediate server, Devolutions Gateway in this example, that proxies the token request to another KDC, which lives on the domain controller.
As Devolutions Gateway is a secure just-in-time lightweight VPN replacement, it is a great option to act as a KDC proxy for remote RDP connections. Devolutions Gateway offers two options: short-lived and long-lived tokens.
Microsoft RDP API hooking should be enabled in Remote Desktop Manager (enabled by default) for Devolutions Gateway connections. This allows continued use when an NTLM downgrade occurs.
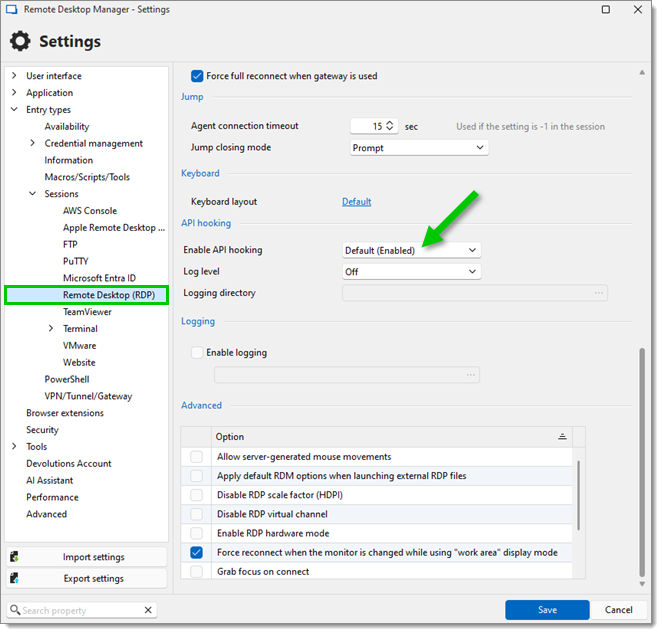
When using a KDC proxy, the recommended default is short-lived tokens dynamically injected by the Devolutions Gateway. These tokens are used in RDP via NLA (Network Layer Authentication) and by the Devolutions web-based sessions, such as WinRM, LDAP, and LAPS. Typical Kerberos tokens are limited to 10 hours by default.
-
In Devolutions Server, head to Administration – Modules – Devolutions Gateway. Then, click the Edit button (pen-shaped icon) on the desired Devolutions Gateway instance.
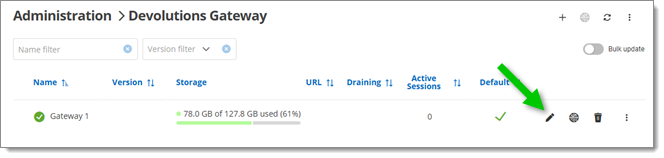
In Devolutions server, edit the desired Devolutions Gateway instance -
In the KDC proxy section, click the Add button (cross-shaped icon). Multiple KDC servers can be added,
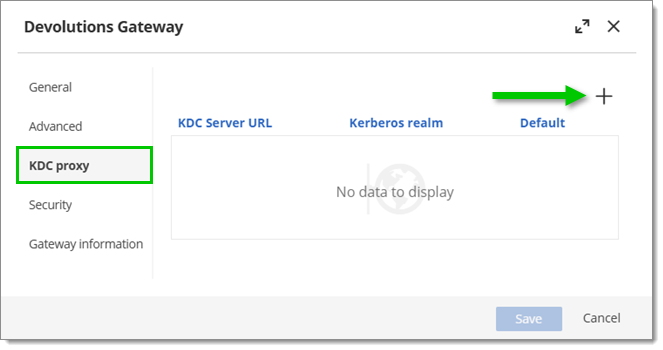
Add a new KDC proxy The connection is matched based on the suffix, e.g., with two server realms named, respectively,
ad.it-help.ninjaandad.contoso.com,machine.ad.it-help.ninjawill automatically use the former suffix, whilemachine.ad.contoso.comwill use the latter. -
Fill out the KDC server URL and Kerberos realm fields. Check Set as default to make all connections use the KDC server URL. Otherwise, only matched realms will be used. Click on Save.
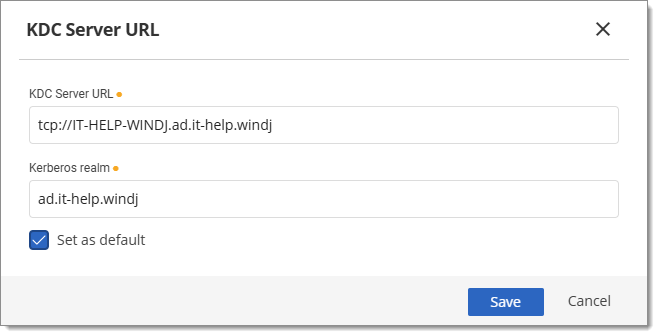
Fill out the KDC server URL fields -
Back in the Devolutions Gateway edit window, go to the Advanced section and make sure that the Force using IP address for RDP connections option is unchecked. Click Save to complete the configuration.
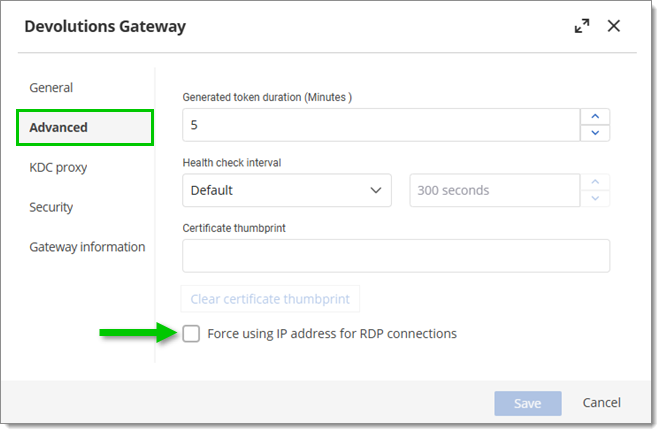
Uncheck the Force using IP address for RDP connections option
Specific tokens can be created to live for 1, 3, and 6 months or a full year. Typically, these long-lived tokens would only be created to then be installed system-wide and used for edge cases where the Devolutions Gateway cannot dynamically inject a short-lived token.
-
In Devolutions Server, head to Administration – Modules – Devolutions Gateway, and click the More button (vertical ellipsis-shaped icon). Select KDC proxy.
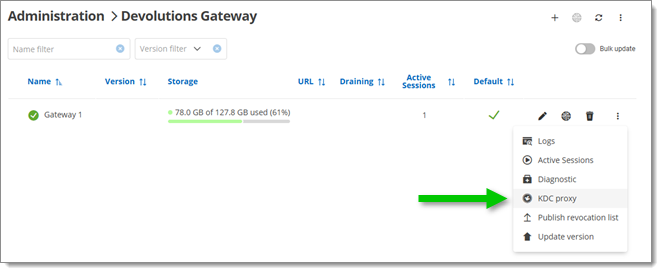
Open the KDC proxy tokens configuration window -
Click the Add button (cross-shaped icon).
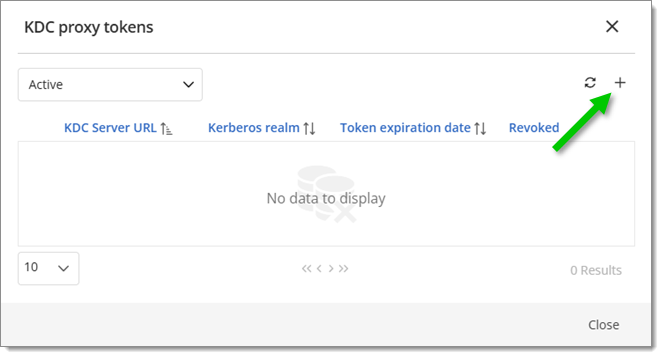
Add a new KDC proxy long-lived token -
Fill out the KDC server URL and Kerberos realm fields, and determine how long the token will live. Click on Add.
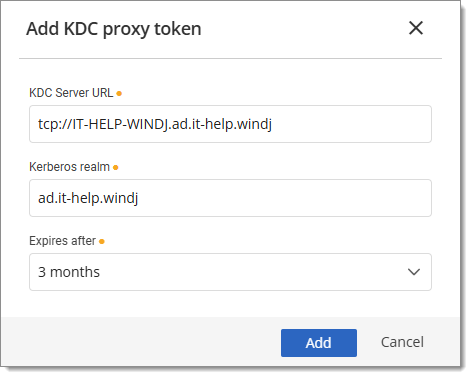
Fill out the KDC proxy token fields -
Once added, download either a PowerShell script or registry file to add the token to the target machine’s registry. Both the registry file and PowerShell file do the same thing, but the PowerShell file also allows running with the
-Uninstallparameter to uninstall, if needed.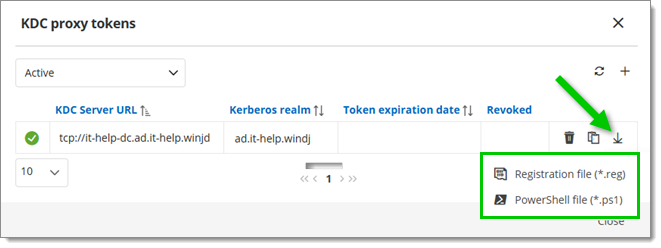
Download PowerShell scrit or registry file
Both scripts configure several registry keys and values:
HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\KerberosHKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\Kerberos\ParametersHKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\Kerberos\KdcProxy\ProxyServers
Within here, the token that was generated will be put with the keys of:
HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\Kerberos\KdcProxyServer_Enabled=1HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\Kerberos\KdcProxy\ProxyServers\{realm name}= Token Value
To remove the KDC configuration from the registry, carefully modify the Windows Registry Editor or launch the previously used PowerShell script using the -Uninstall parameter.
Adding users to the Protected Users group in Active Directory disables NTLM, often breaking RDP for remote sessions. Devolutions Gateway fixes this by acting as a KDC proxy, enabling Kerberos authentication even without direct domain controller access. In Remote Desktop Manager Windows, RDP API hooking must be enabled to support short-lived Kerberos tokens and restore RDP functionality securely.